The Blog
Research

Phishing Simulation Metrics Beyond Click Rate
Click rate is deceptive. Use report rate, time-to-report, repeat risk, and difficulty scoring to track real phishing simulation progress.
Gina Jee
Latest Blog Posts
Research
Scaling a Python Org: Fast Builds, Consistent Environments, Happy Engineers
How Doppel migrated to uv workspaces, Docker, and Cloud Run to build a foundation for scaling
Krish Masand
Research
Cyber Threat Landscape Analysis for Brand Risk Teams
Learn how brand risk teams map attack vectors, track shifting threats, and turn cyber threat landscape analysis into faster takedowns.
Gina Jee
Company
Operation Doppelbrand Is Not Doppel, But It Signals a Growing Threat
We’re aware of recent reporting about a new brand impersonation campaign called Operation DoppelBrand. While the name bears a resemblance to Doppel, we want to clearly state that this campaign is not affiliated with nor connected to our company in any way.
Kevin Tian

Blog
Phishing Simulation Metrics Beyond Click Rate

Blog
Scaling a Python Org: Fast Builds, Consistent Environments, Happy Engineers
Blog
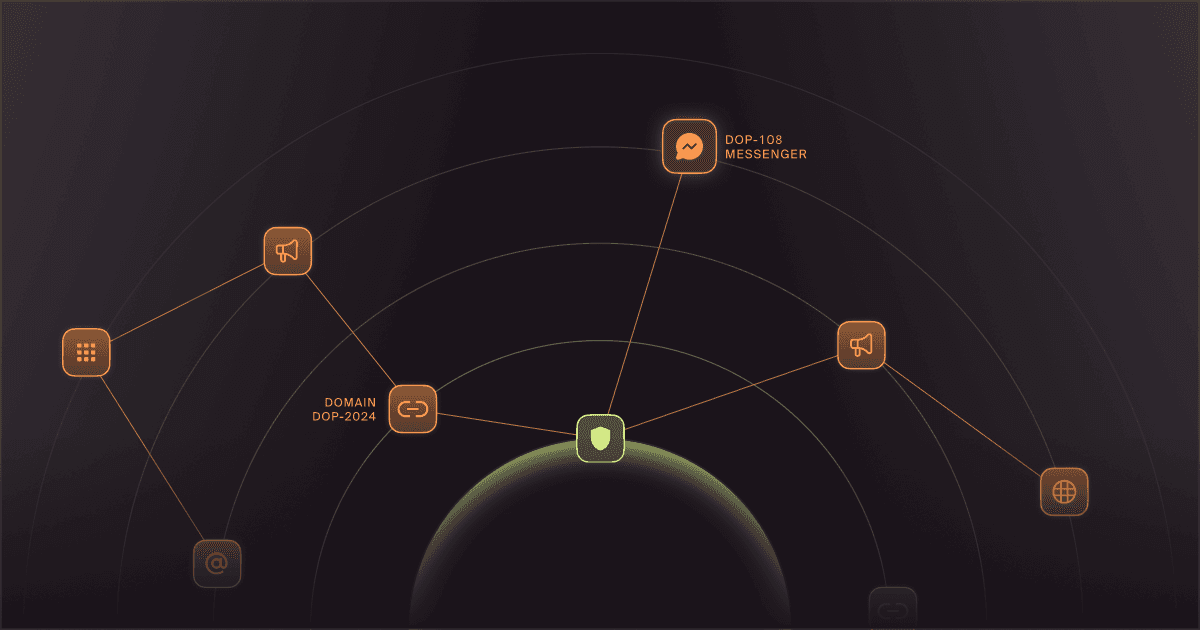
Cyber Threat Landscape Analysis for Brand Risk Teams

Blog
Operation Doppelbrand Is Not Doppel, But It Signals a Growing Threat
Blog
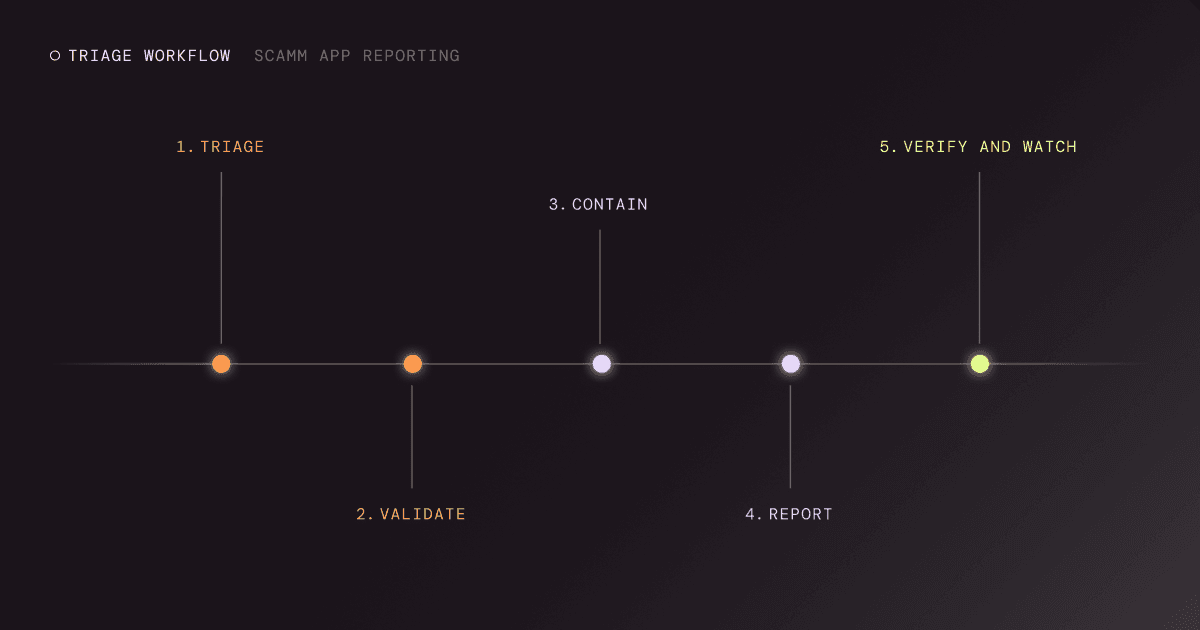
Scam App Reporting: Remove Fake Apps Fast
Blog
Doppel and Modern Social Engineering Defense
Blog
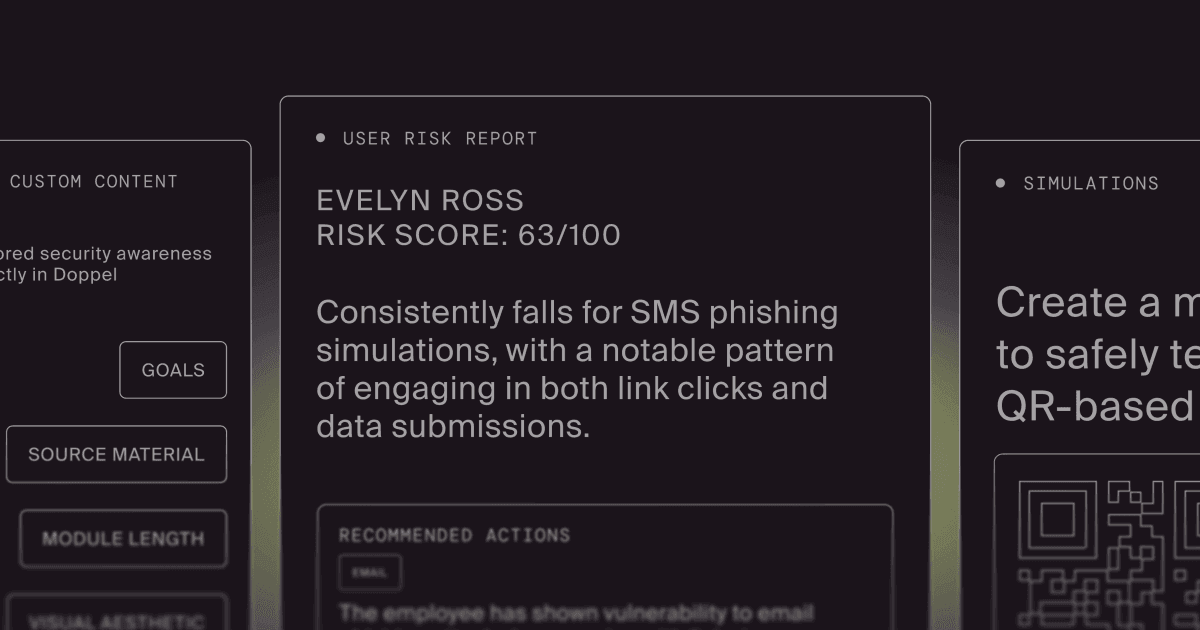
New HRM Capabilities Built for How Attacks Actually Happen

Blog
Impersonation Risk Assessment for Brands

Blog