Brand AbuseBox
Empower people. Operationalize behavior. Dismantle infrastructure.
An AI-powered engine that converts public threat reports into global impersonation takedown.
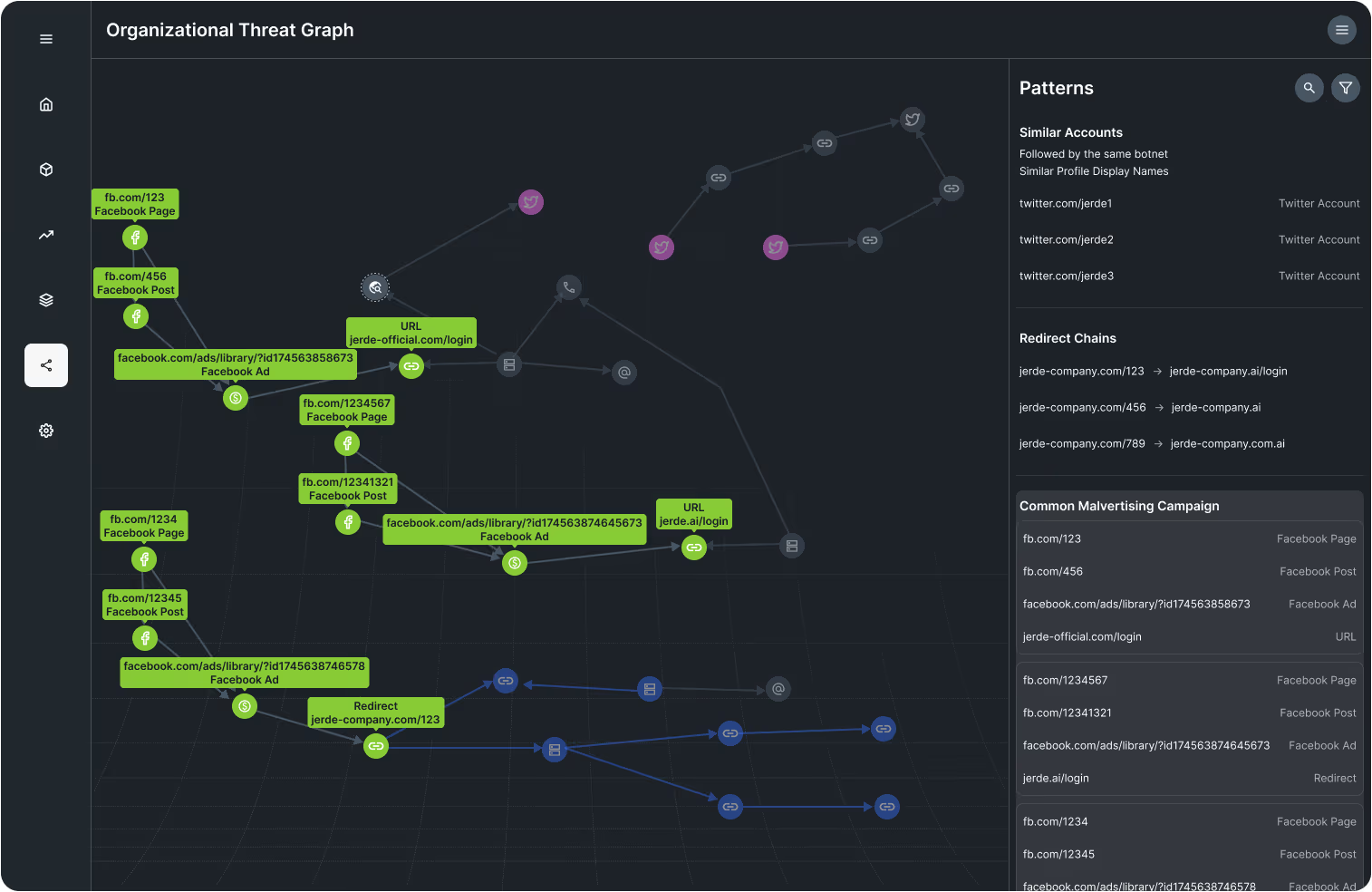
Brand AbuseBox transforms public reports – abuse inboxes, tickets, or complaints – into a direct intelligence pipeline.
Brand AbuseBox connects customer-detected scams to Doppel Vision’s enforcement capabilities. It doesn’t stop at alerting–it identifies infrastructure, correlates across channels, and initiates immediate disruption at scale.
Why it matters:
- Scams are often caught by people before platforms. Brand AbuseBox bridges that gap.
- Manual queues delay action. We automate enforcement.
- Many email security and DRP tools only detect. Brand AbuseBox dismantles.
- The result? A threat isn’t just flagged. It’s neutralized–across every channel it touches.
Customer-reported scams, resolved at scale.
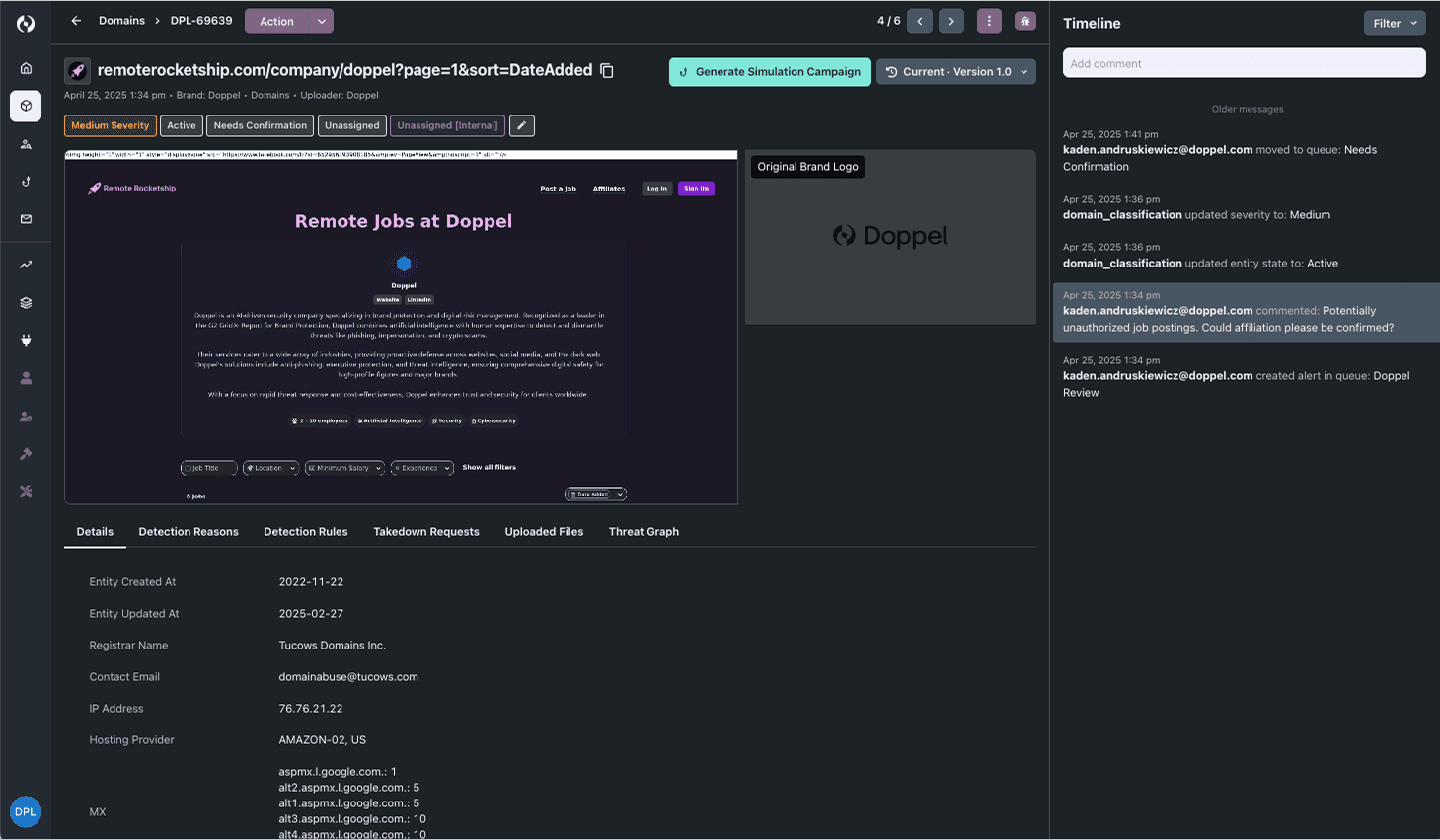
How it works
- Signal Ingestion – Public abuse inboxes and reporting tools feed into Doppel Vision.
- AI Parsing + IOC Extraction – Links, domains, phone numbers, and threat artifacts are extracted and analyzed.
- Cross-Channel Correlation – Doppel Vision links each report to broader attacker infrastructure.
- Automated Enforcement – Validated threats are takedown-ready in seconds.
- Shared Threat Grid Contribution – Every takedown makes future detection faster for everyone.
Turn your public signals into a private advantage
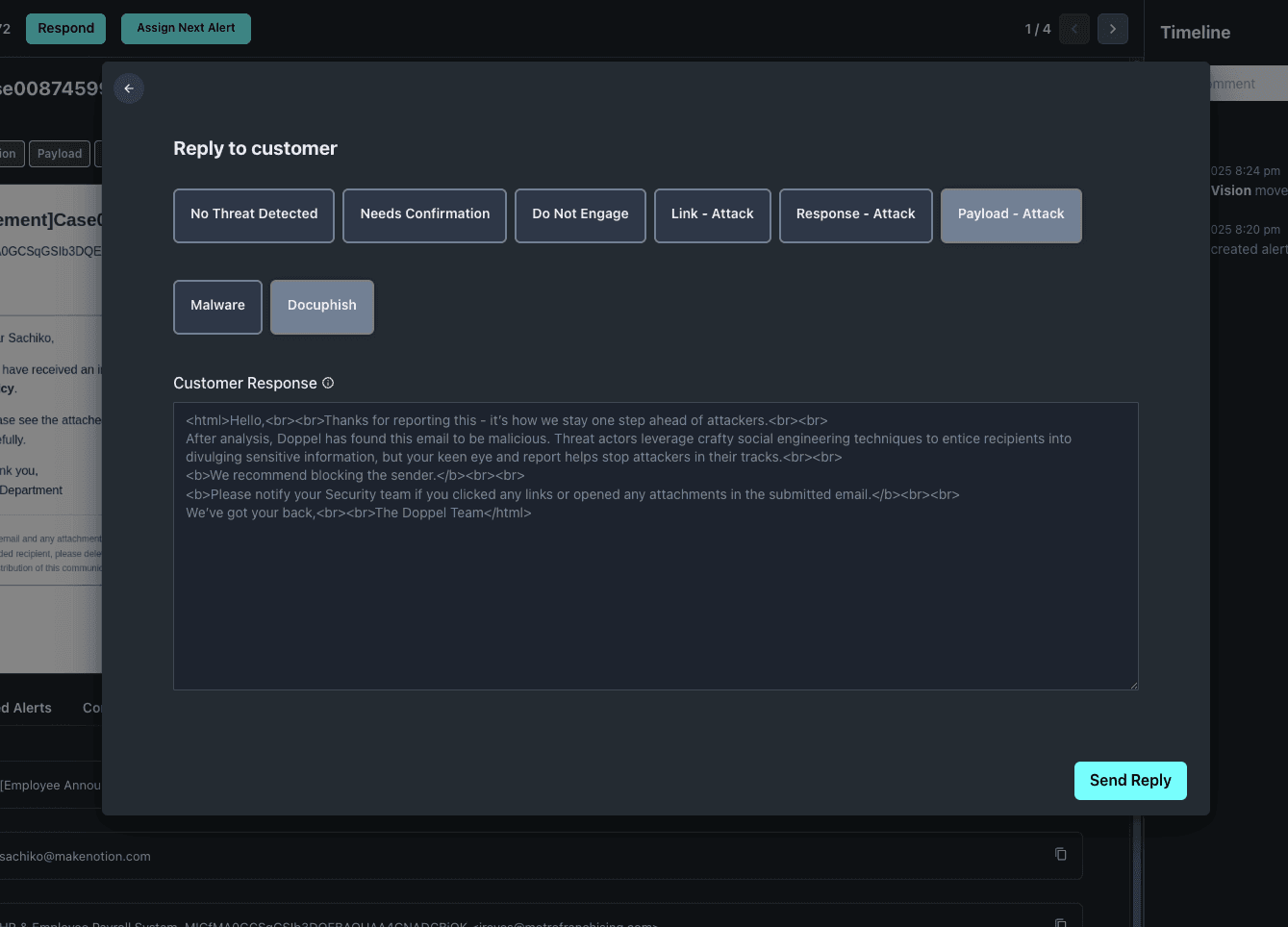
Make every customer report a reason attackers can’t rebuild.
Threats don't just get seen. They get stopped. Brand AbuseBox transforms your abuse inbox from a dead end into a disruption engine. Every email makes your defense stronger-and impersonation harder to pull off next time.
What makes it different:
- Public signal intake with no integration lift
- AI-enhanced, analyst-verified correlation
- Infrastructure takedown–not ticket generation
- Direct connection to Our Threat Grid
- Precision response at scale–94.7% validation fidelity
Frequently Asked Questions
What is AbuseBox?
AbuseBox is Doppel’s AI-powered solution that transforms employee- and customer-reported phishing or abuse emails into actionable intelligence. Instead of letting reports sit in a shared inbox, AbuseBox ingests, validates, and escalates threats for rapid takedown.
How does AbuseBox reduce analyst workload?
Traditional phishing inboxes drown SOCs in noise. AbuseBox uses agentic AI to triage reports automatically, correlating duplicates and linking signals to attacker campaigns. This eliminates repetitive review work and accelerates incident response.
What happens to a reported email inside AbuseBox?
Each report is:
- Ingested and parsed by AI.
- Validated for malicious indicators.
- Correlated with Doppel’s Threat Graph to check for related campaigns.
- Escalated into automated takedown workflows if confirmed malicious.
How does AbuseBox integrate with security operations?
AbuseBox connects to SIEMs and SOAR tools (e.g., Splunk, Sentinel, Tines). Reports can trigger playbooks, feed into dashboards, and be audited end-to-end for compliance.
How does AbuseBox strengthen long-term resilience?
Every user report feeds back into Doppel’s detection models and Simulation engine, helping organizations improve their phishing resilience. Over time, AbuseBox not only clears noise but also makes threat detection sharper and faster.

