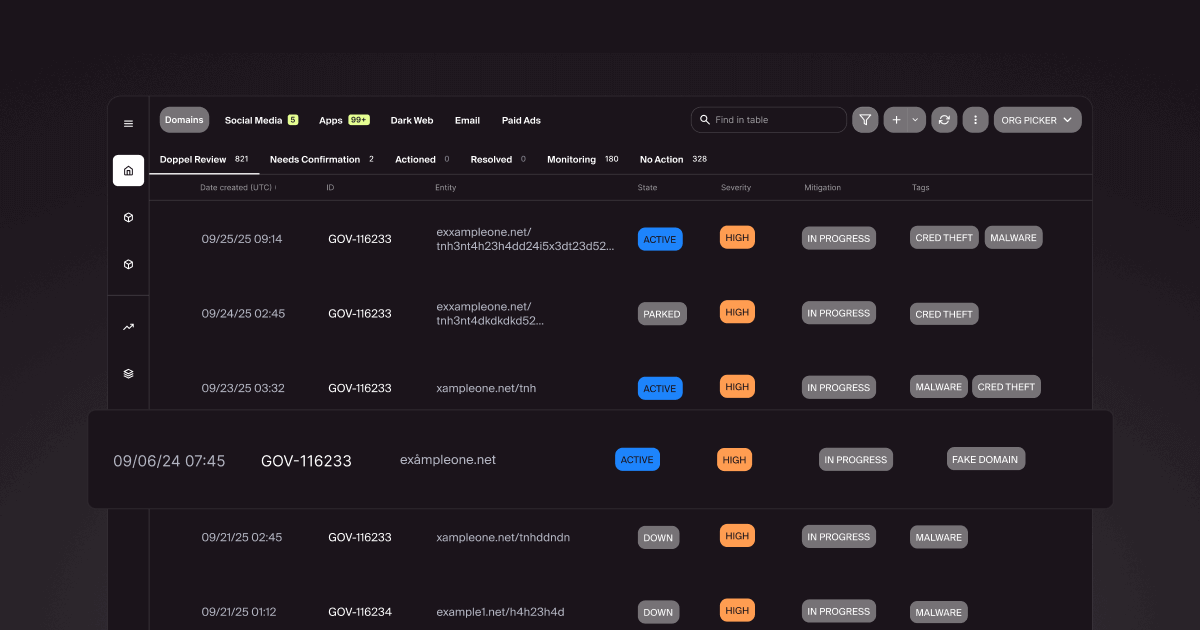
Fake domain impersonation is one of the most common and damaging tactics used by scammers. Every week, thousands of fraudulent domains appear online, each designed to mimic trusted brands and trick unsuspecting customers. Some redirect to phishing sites. Others clone a brand’s website to collect credentials, harvest payments, or spread malware.
As brand protection professionals, we see firsthand how damaging these campaigns can be. They create confusion, drain consumer confidence, and make it harder for legitimate communications to be trusted. In this article, we’ll take a close look at what fake domain impersonation removal entails, why it matters, and how modern threat-intelligence tools can accelerate and enhance the process.
Why Fake Domain Impersonation Matters
Fake domains have evolved far beyond basic typosquatting. Attackers now register highly sophisticated look-alike URLs that mimic legitimate brands with incredible accuracy. This problem affects every industry, from finance and retail to healthcare and technology, and it’s not slowing down. Fake domains are one of the most visible parts of digital risk protection, because they sit directly in the path of your customers.
Protecting your organization’s domain presence is no longer optional. It’s an essential component of digital risk management and customer trust. Fake domains can damage brand reputation long before a customer reports a phishing attempt, and by the time a threat is visible, the harm is already done. Our brand protection platform maps how fake domains are connected to scam ads, spoofed accounts, and other external threats.
The Changing Landscape of Domain-Based Attacks
In the past, domain impersonation relied on simple spelling errors, such as “gooogle.com” or “amazzon.net.” Now, attackers use internationalized domain names (IDNs) with non-Latin characters, subdomain spoofing, and brand extensions that appear legitimate at a glance.
For example, “yourbrand-secure[.]com” or “yourbrånd[.]com” can pass unnoticed in an email or ad click. These deceptive variations can even fool security-aware users, thereby increasing the likelihood of credential theft and fraud.
Business Impact and Brand Risk
A single fake domain can lead to a cascade of losses. Customers who encounter a cloned site often believe they’re interacting with the authentic brand. When they enter personal or payment information, that data is immediately compromised.
Even if the brand itself isn’t directly hacked, customer trust is eroded. Rebuilding confidence after a publicized impersonation incident takes time, resources, and transparency. It also affects sales performance, marketing ROI, and long-term brand perception.
Why Traditional Defenses Fall Short
Many companies still rely on manual searches or user reports to find fake domains. The problem is that attackers automate their campaigns. They can deploy hundreds of look-alike domains overnight and discard them after a few days.
By the time a brand identifies and reports one domain, another wave is already live. Automated monitoring and proactive removal are the only ways to keep pace with today’s impersonation volume.
The Anatomy of a Fake Domain Attack
Understanding how fake domain campaigns work helps brands anticipate threats before they escalate. Attackers follow a relatively predictable process, although each phase can be automated or disguised to conceal activity.
Domain Registration and Look-Alikes
Cybercriminals often use bulk registration platforms or stolen payment credentials to register domains that resemble legitimate brands. They may use alternative top-level domains (.net, .io, .shop) or swap characters for similar-looking ones to bypass filters.
Once registered, these domains become the foundation for phishing websites, scam portals, or malicious redirects.
Hosting, Content, and Phishing Set-Up
After domain registration, attackers deploy cloned versions of a brand’s website. They copy logos, color palettes, and layouts to appear authentic. Some even integrate fake chatbots or customer service pages to maintain credibility.
The domains are then promoted through social media ads, fake customer support channels, or phishing emails. The result is a seamless illusion that leads unsuspecting users to enter private data.
Detection Evasion and Rapid Mutation
Many impersonation campaigns are short-lived but recurring. Once a fake domain is reported, it’s often replaced by another variation within hours. Attackers use content cloaking and fast-flux DNS techniques to evade automated detection.
This constant turnover makes manual investigation nearly impossible, reinforcing the need for automated detection systems and immediate takedown workflows.
How We Approach Fake Domain Impersonation Removal
We approach fake domain impersonation removal as a continuous process, not a one-time event. Effective removal combines advanced detection, forensic investigation, and coordinated enforcement across domain registrars and hosting providers. We use automation to detect and initiate the takedown of fake domains before users are deceived.
The goal is to reduce the attack window. Every minute a fake domain remains online increases the potential for customer harm. Our brand protection capabilities connect the removal of fake domain impersonation with monitoring across social media, ads, the dark web, and mobile apps. We correlate fake domains with related impersonation campaigns across these channels.
Detection and Prioritization
Our monitoring systems continuously scan for domain variations that resemble a client’s brand name, products, or key web assets. We track new registrations, SSL certificate issuances, and DNS changes to detect threats early.
Once detected, domains are prioritized based on their risk level. For example, an inactive parked domain might be flagged for observation, while an active phishing site gets immediate escalation.
Evidence Collection and Escalation
Before requesting a takedown, evidence must be collected. We compile screenshots, WHOIS records, hosting information, and examples of impersonated content, ensuring that registrar abuse teams and hosting providers can take prompt action.
Accurate evidence increases success rates for takedown requests, avoids unnecessary disputes, and creates an audit trail for brand protection reports.
Rapid Takedown and Monitoring
Once verified, we initiate takedown requests through registrars, ISPs, and cloud providers. Some cases involve DNS sinkholing or traffic blocking to limit damage while the domain is removed.
Post-removal monitoring ensures that the same scammers don’t re-register the domain or move the operation to a new TLD (top-level domain). Continuous oversight prevents recurrence and strengthens long-term protection.
Integration with Broader Brand Protection Strategy
Fake domain impersonation removal is most effective when integrated into a broader digital risk protection (DRP) program. That includes monitoring for impersonation on social media, marketplaces, and paid ads. Read more about how digital risk protection fits into your cybersecurity strategy to understand how domain takedowns strengthen your overall security posture.
By combining domain removal with cross-channel intelligence, brands can track scammers across their entire digital footprint.
Best Practices for Organizations Facing Fake Domain Threats
A successful fake domain mitigation strategy combines proactive registration, intelligent monitoring, and fast-response coordination across internal teams. The following best practices help organizations stay one step ahead.
Register Key Variants and Set Policies
You can’t buy every domain variation, but registering common misspellings, alternate TLDs, and high-risk terms related to your brand can block a large percentage of attacks. Maintaining a defensive domain portfolio is a small cost compared to the reputational damage from an impersonation campaign.
Implement Email Authentication and Domain Controls
Even if your primary concern is web impersonation, enforcing SPF, DKIM, and DMARC policies strengthens your domain credibility. These protocols help ensure that legitimate messages are delivered while fraudulent ones are blocked or flagged.
Automate Monitoring and Takedown Workflows
Manual monitoring can’t keep pace with the sheer number and speed of new threats appearing every day. Automating monitoring and takedown workflows ensures faster, more consistent results.
Collaborate Across Teams
Brand impersonation is not just an IT issue. It involves various departments, including legal, marketing, security, and customer support. Cross-functional coordination ensures that once a fake domain is removed, customer communications and search visibility are updated quickly. When customers report suspicious links, Brand AbuseBox converts those reports into structured cases that are fed directly into our takedown workflows.
Measure and Iterate
Track data such as detection speed, takedown success rate, and recurrence frequency. These metrics provide a clear picture of the program’s effectiveness, guiding ongoing improvements. Incorporating external digital risk testing helps assess how well your defenses perform against simulated domain impersonation attacks before they occur in the real world.
Looking Ahead: Emerging Threats and Trends
Fake domain impersonation is changing quickly, with new tactics and scams appearing all the time. Security professionals must anticipate how technology alters the threat model and adjust accordingly.
Two trends stand out: the use of AI and the increasing sophistication of homograph attacks.
AI-Enabled Rapid Domain Abuse
Attackers now use AI to automate domain generation, website cloning, and image creation. These tools allow them to produce hundreds of convincing fake websites in minutes. The automation also enables them to quickly replace domains that are taken down, keeping campaigns alive indefinitely. Not only are attackers using AI, but we also utilize it in our own detection workflows, enabling us to counter these tactics at scale.
Homograph and Unicode Domain Abuse
Unicode characters that resemble Latin letters can make homograph attacks especially deceptive. For instance, a Cyrillic “а” may appear identical to an English “a.” This trick creates domains that visually resemble legitimate ones but are functionally distinct, thereby bypassing many detection filters.
Cross-Channel Impersonation Campaigns
Fake domains often act as hubs for broader impersonation efforts. Attackers link them to fake social media pages, mobile apps, and advertising campaigns. Without a coordinated response, removing one fake domain won’t eliminate the entire operation.
Key Takeaways
- Removing fake domain impersonation is essential for protecting customers and preserving brand integrity.
- Detection must be proactive and automated to stay ahead of high-volume, short-lived domain campaigns.
- Successful removal relies on comprehensive workflows that include evidence collection, registrar escalation, and post-takedown monitoring.
- Integrating domain protection into a complete digital risk management strategy delivers stronger results than isolated efforts.
Strengthening Your Defense with Fake Domain Impersonation Removal
Fake domain impersonation removal is a proactive defense that safeguards your customers and protects the trust your brand has earned. By identifying and taking down look-alike domains early, you prevent scams before they spread and stop attackers from profiting off your reputation. Investing in fake domain impersonation removal helps your organization maintain credibility and security and stay one step ahead of new digital threats.
Take action before scammers do. Book a demo to learn how our brand protection platform streamlines fake domain impersonation removal and strengthens your overall digital defense strategy.