In 2025, cybercriminals aren't breaking in—they're logging in. Powered by generative AI, attackers bypass firewalls by exploiting human trust. From deepfakes and impersonation to multi-platform manipulation, modern threats don’t target infrastructure first—they target people.
Doppel’s whitepaper, Defining the Next Era of Cybersecurity: The Case for Social Engineering Defense, introduces Social Engineering Defense (SED): a transformative framework designed to confront this growing crisis.
The Cost of Social Deception Is Real—and Rising
Social engineering is no longer a fringe tactic; it's the dominant cybercrime model. At an average cost of $1.6 million per incident, these attacks affect every layer of the enterprise. Executives face personal and reputational risk, employees fall prey to credential theft, and brands suffer irreversible trust damage.
AI-powered deception also invites mounting legal and regulatory scrutiny. Yet most security systems—designed for malware, not manipulation—are unequipped to respond.
Why Traditional Social Engineering Defenses Fail
Legacy security stacks focus on detection, not disruption. They isolate threats in silos, depend heavily on human triage, and treat social engineering as merely a phishing issue. Meanwhile, adversaries use AI to scale deception rapidly across LinkedIn, Telegram, TikTok, WhatsApp, and encrypted platforms. Current Digital Risk Protection (DRP) tools may spot surface symptoms—like spoofed sites or accounts—but they can't connect dots across channels or take down attacker infrastructure.
Introducing Social Engineering Defense (SED)
SED isn’t just a framework—it’s a strategic shift. Built for speed, scale, and precision, SED transitions security from reactive response to real-time disruption. It’s grounded in three pillars:
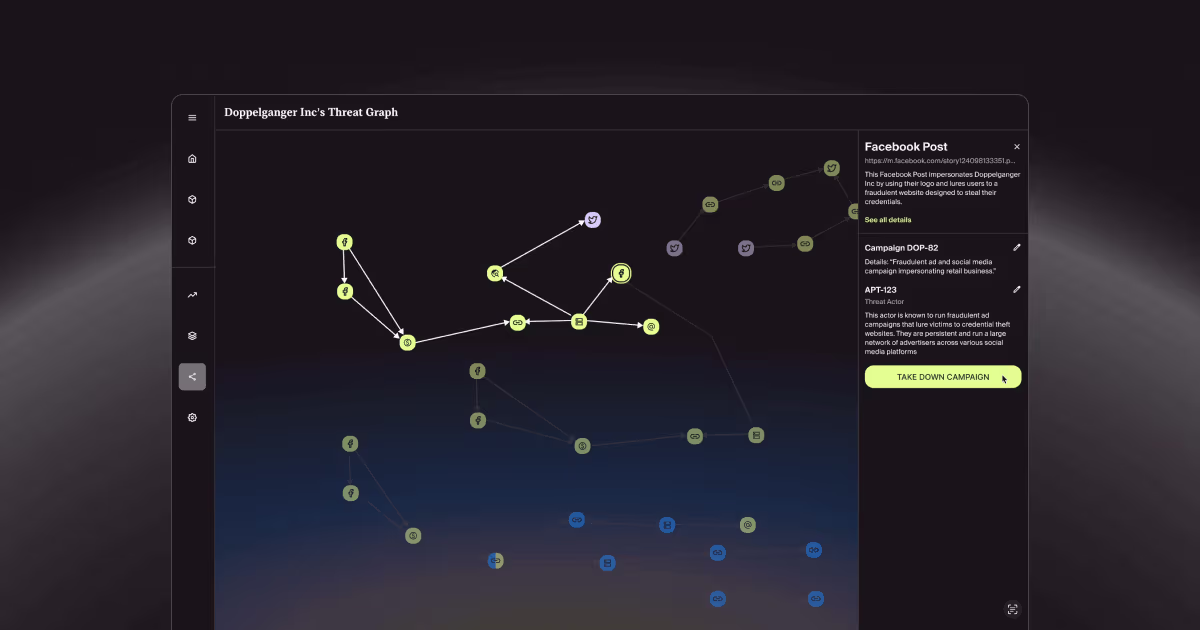
- Networked Intelligence: By mapping attacker ecosystems in real-time, SED unifies threat signals—domains, phone numbers, scam content—into a constantly evolving threat graph. Shared intelligence across enterprises accelerates detection and makes every disruption smarter.
- Multimodal, Multichannel AI: Social engineering is fluid, and so must be detection. SED uses AI to recognize patterns across voice, video, text, and behavior, even on unstructured or fringe platforms. It detects intent, not just content, reducing dwell time and exposing synthetic manipulation before damage is done.
- Infrastructure Takedown: True defense dismantles the business model behind deception. SED enables automated removal of phishing kits, fake sites, and spoofed assets, making attacks expensive to launch and difficult to sustain. The result: attackers lose their advantage of scale.
SED: The Strategic Imperative
The threats we face demand more than new tools—they require a new mindset. SED reframes cybersecurity as a disruption mission, empowering organizations to strike at the root of deception rather than chase its symptoms. It offers reduced analyst workload, faster response cycles, and proactive brand protection.
For CISOs and security leaders, the question is no longer “Can we detect the attack?” but “Can we dismantle the infrastructure behind it?”
The time to detect is shrinking. The time to disrupt is now.
Learn how your organization can proactively defend what’s real and disrupt what’s not.
Book a demo: www.doppel.com/request-a-demo