Introducing the Doppel Threat Graph
Modern deception doesn’t happen in silos, neither should your defenses.
The Doppel Threat Graph was built to expose the full architecture of an impersonation campaign. It connects every spoofed domain, fake profile, impersonated ads and malicious texts into a single, interactive graph. Now, you can see the attack as a system, not just signals scattered across the web. Powered by AI and evolving with networked intelligence, the Threat Graph reveals how infrastructure is reused, scaled and spread– and has the ability to take it down. Today this feature is available for all customers in the Doppel Vision Platform.
This isn't just threat intelligence, it’s threat elimination with graph-driven defense.
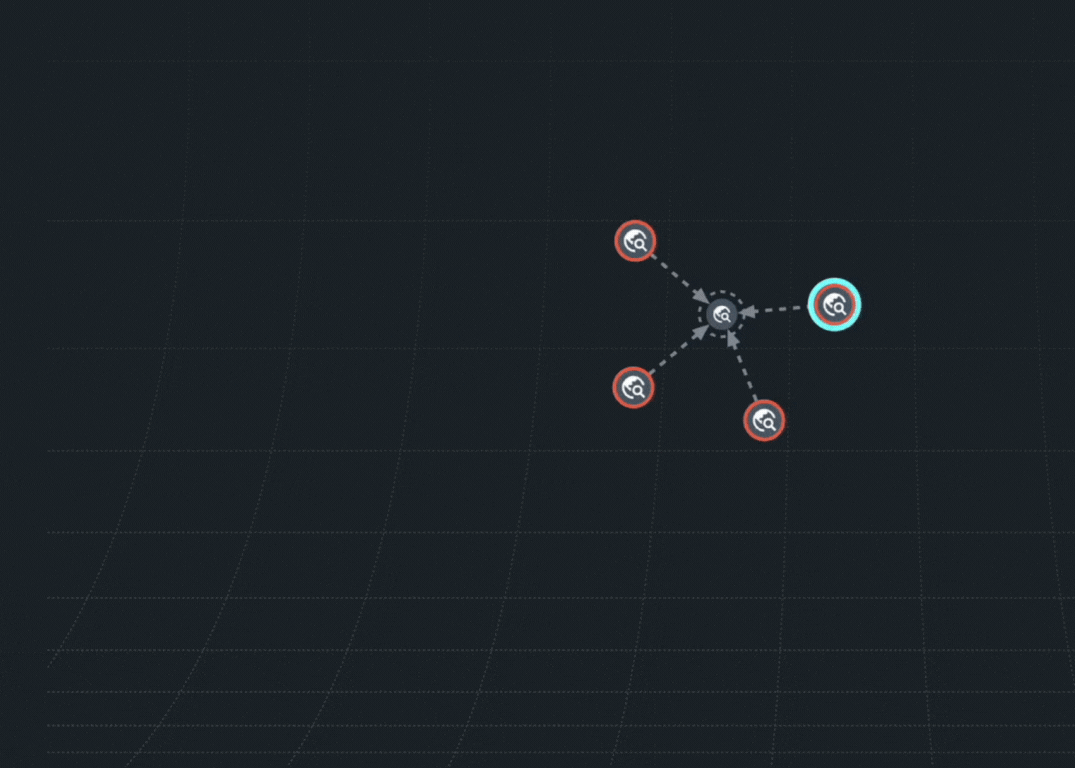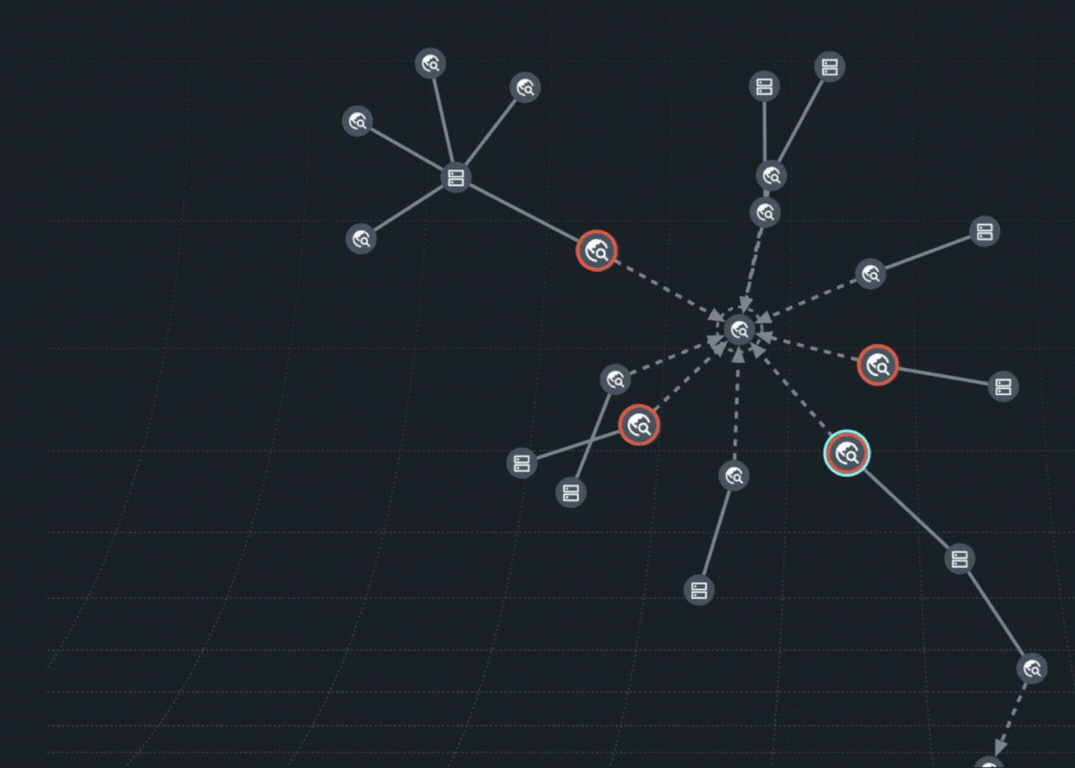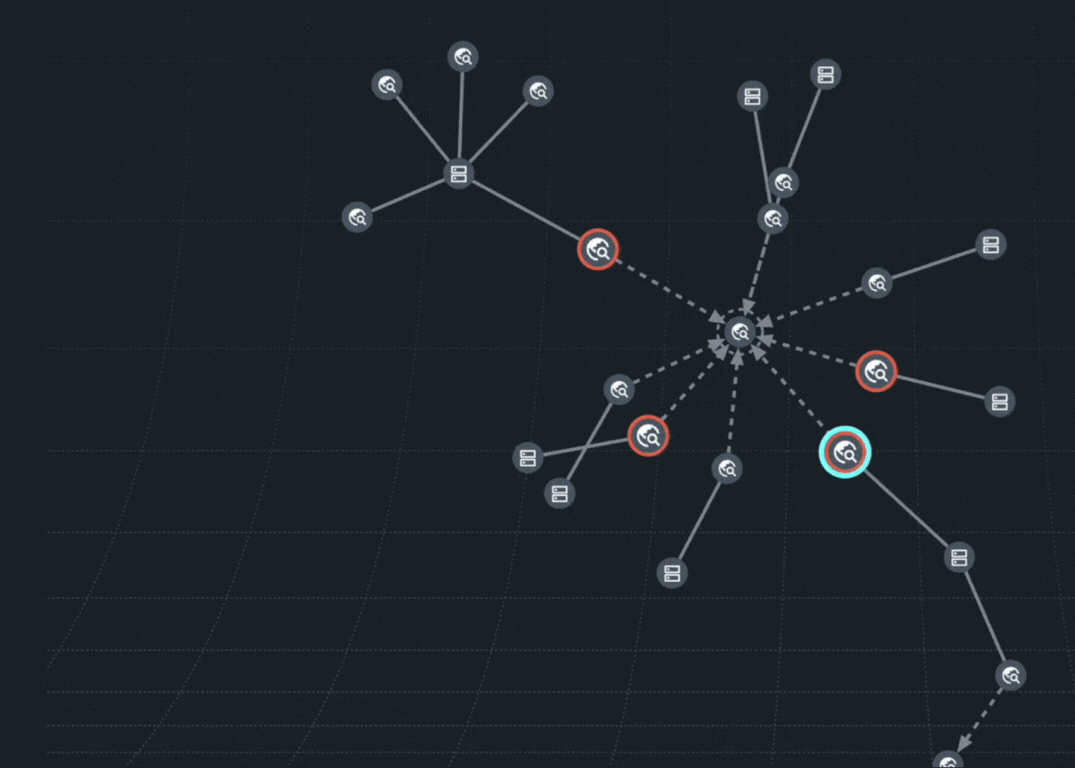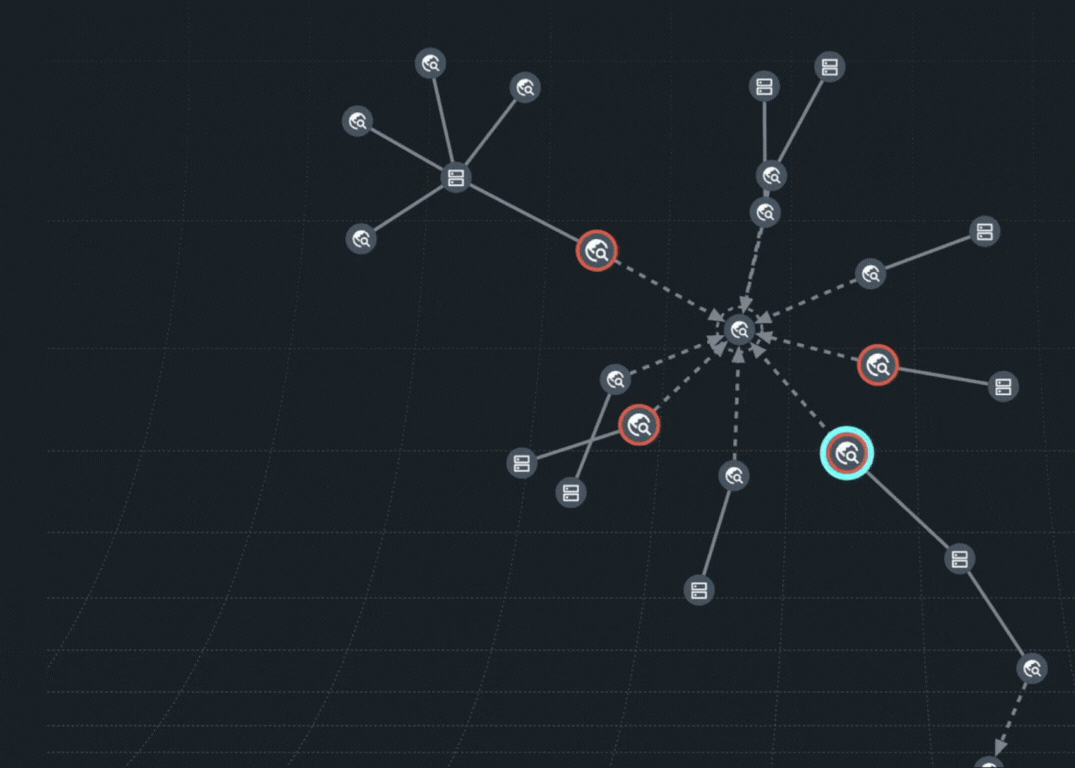
What Is Graph-Driven Defense?
Attackers today launch full-scale multi-channel campaigns that span email, paid ads, WhatsApp, LinkedIn, Telegram, and even voice. They reuse infrastructure. They automate distribution. And they evolve faster than most security teams can triage.
Graph-driven defense is how you fight back.
It’s not a dashboard. It’s not a feed. It’s a model of how modern attacks work– and how to dismantle them before they scale.
At Doppel, graph-driven defense means mapping every spoof, scam, redirect, and impersonation attempt into one visual system– then tearing that infrastructure down at speed.
Here’s what makes it different:
Multi-Channel Visibility, One View
From domains to DMs to deepfakes– every surface, every signal, one graph.
Most tools give you visibility into one part of the attack– maybe domains, maybe email, maybe dark web chatter. Doppel sees the entire ecosystem.
We correlate impersonation infrastructure across:
- Paid ads & SEO abuse
- Telegram bots & WhatsApp scams
- Fake social profiles (LinkedIn, Instagram)
- Spoofed apps & SMS phishing
- Deepfake campaigns and more
One platform replaces 4–5 disconnected point tools.
More importantly, it shows you where threats actually live, not just where your current tools are built to look.
AI-Correlated Campaign Intelligence
We connect the infrastructure behind every fake, spoof, and scam– so you don’t have to.
Impersonation attacks rarely happen in isolation. A spoofed email often links to a cloned domain. That domain might appear in a paid search ad. A deepfake audio message might reference the same Telegram handle from a fake app review. Our real-time Threat Graph connects it all.
AI-powered correlation maps out the entire attack campaign and prioritizes what matters most based on cost, reach, and reuse patterns.
That means:
- Faster root cause detection
- No more chasing artifacts one by one
- Smarter SOC automation from signal to resolution
In short: less noise, more insight.
End-to-End Threat Disruption
We don’t just show you the threat. We take it down.
Too many platforms leave response to your team or want to sell you managed services. They show you the threat, but they won’t do anything about it.
Doppel does.
Every node in the Threat Graph is operational– a domain that can be taken down, a profile that can be escalated, a campaign that can be neutralized.
And unlike legacy DRP or intel tools, we don’t stop at alerting.
Our internal SOC, powered by both AI agents and real humans, executes every takedown, escalation, and follow-up across registrars, ad networks, telcos, platforms, and more.
That means:
- Reduced analyst load (fewer alerts, no triage backlog)
- No need for internal takedown teams
- Auditable workflows for governance and compliance
Why It Matters Now
Graph-driven defense is more than a platform feature, it’s a response model for the era of AI-powered deception.
Attackers can scale faster and cheaply. If your security, fraud, and brand teams are still working from isolated alerts, you’re not defending trust – you’re chasing shadows.
Don’t just detect deception. Dismantle it.
Learn more about graph-driven defense and our whole suite of solutions. Schedule a demo or reach out to your CSM for more information.