Your brand is being impersonated across domains, social profiles, paid ads, app stores, and other third-party platforms that your team doesn't have time to monitor. Attackers keep recycling the same playbook with new wrappers, and they are faster than your inbox.
That’s the problem CTI should solve for brand protection. Not by generating another feed of “interesting” indicators, but by turning detection into action. Specifically, detection, triage, and takedown, with enough context so your team does not drown in false positives or ticket ping-pong
TL;DR: CTI automation for brand fraud is a detection-to-takedown system. It automatically collects and enriches impersonation signals, correlates them into campaigns, prioritizes by harm and exposure, and routes high-confidence cases into repeatable enforcement workflows with guardrails and human review for edge cases.
What Is Cyber Threat Intel Automation for Brand Fraud Protection?
Cyber threat intel automation (CTI automation) for brand fraud protection is the practice of automatically collecting, enriching, prioritizing, and routing brand impersonation signals into operational workflows that result in responses. In practice, that means correlating spoofed domains, fake profiles, scam ads, and malicious messaging into campaigns, then driving takedowns with consistent evidence and human oversight for edge cases. The goal is fewer live impersonation assets, shorter time to takedown, fewer customers pulled into scams, and less repeat work when the same actors reappear under new domains and accounts.
In practical terms, CTI automation connects three things that often live in separate tools and teams. External monitoring, internal decisioning, and response. It pulls signals from the messy outside world, adds context so responders can act with confidence, and pushes the right work to the right place with clear urgency. If your current “intel” still requires someone to copy links into a spreadsheet and message legal for a template, you do not have CTI automation. You have a manual pipeline with a dashboard on top.
What Makes Brand Fraud CTI Different from Classic CTI?
Brand fraud CTI focuses on attacker infrastructure and distribution channels, not just malware families and exploit chains. You care about where customers are being redirected, what identity is being copied, and how fast the campaign is scaling through ads, social, SMS, marketplaces, and app stores. A stolen login is bad. A stolen login, a cloned support center plus a paid ad campaign are worse. The unit of work is a campaign.
Unlike classic CTI, where the output is often analysis or detection context for internal defenders, brand fraud CTI must produce third-party-enforceable evidence that results in assets being removed.
It also has a different bar for evidence. In enterprise CTI, you might tolerate lower confidence indicators because they’re one input among many in an SOC workflow. In brand protection, you often need greater confidence and clearer proof, as remediation depends on third parties—registrars, platforms, hosting providers, and app stores. If you can’t package evidence in a way those parties accept, the best intel in the world becomes a “known issue” that stays live.
Where CTI Automation Fits in Brand Protection
CTI automation sits between monitoring and response, serving as the glue that keeps the work from stalling. Monitoring answers, “What is out there?” CTI automation answers, “What does it mean, how bad is it, and what do we do next?” Response answers, “How do we remove it and prevent re-entry?”
In a mature program, CTI automation becomes the control plane for brand fraud operations. It normalizes incoming signals across channels, applies consistent scoring and routing, tracks outcomes, and uses those outcomes to improve the next cycle. You stop treating brand abuse as a series of one-off fires and start treating it like an operational pipeline that should get faster every week.
Why Does Manual CTI Break Down So Fast?
Manual CTI breaks down because brand fraud campaigns scale faster than human review can keep up, and they are engineered to waste your time. A single actor can spin up a cluster of lookalike domains, generate hundreds of ad variations, and rotate social handles faster than a team can validate and submit takedowns. Even if you have great analysts, you can’t out-click an automated adversary.
There is also a hidden tax. Every manual step adds latency, and latency gives attackers more time to harvest victims. When you’re dealing with customer-targeted phishing, fake support, or payment diversion, hours matter. If it takes two days to confirm and route an asset, the campaign has already moved on, and your takedown is basically a cleanup exercise.
In short, manual CTI fails because it can’t match attacker speed, and every hour of delay increases victim exposure.
The Three Common Failure Modes
Manual workflows fail in three predictable ways.
Alert hoarding: Your queue becomes a museum of “things we should look at.” Analysts keep collecting because collecting feels productive. Meanwhile, the backlog grows, and the team starts normalizing missed coverage.
Context gaps: You see a bad domain, but not the campaign behind it. Without correlation, responders can’t tell if they are dealing with a single throwaway site or a multi-channel operation. That uncertainty creates cautious behavior, which means slower action.
Slow handoffs: Evidence gets scattered across screenshots, spreadsheets, ticket comments, and chat threads. Legal needs a packet. Security needs confirmation. Brand needs to align its messaging. Support needs a macro. Everyone waits on everyone, and attackers love the dead time.
What Should CTI Automation Actually Automate?
CTI automation should automate the repeatable steps that slow you down and introduce inconsistency: collection, enrichment, correlation, prioritization, and the mechanics of takedown execution. Humans should focus on campaign-level strategy. If your best people are spending their day taking screenshots and chasing redirect chains, that’s a tooling problem.
The trick is to automate the parts that create leverage. That usually means automating the steps that happen for every case. You want to remove friction from the common path so your team has the time to handle the hard cases where judgment actually matters.
Automate the Boring Parts First
If a step happens the same way 80 percent of the time, automate it. If it varies each time, standardize it until it is automatable. The fastest wins usually look like this.
- Automated collection across domains, social, ads, apps, and marketplaces
- Automated screenshot capture and content rendering for evidence
- Automated URL expansion and redirect chain resolution
- Automated brand element matching, such as logos, product names, copy, and support language
- Automated enrichment with WHOIS, TLS certificates, hosting, and registrar data
- Automated deduplication so the same asset does not show up as five “new” alerts
Once you have that foundation, correlation and prioritization get dramatically easier because you are working with clean, consistent inputs.
Keep Humans Where Liability Lives
Policy calls, escalation paths, and judgment-heavy approvals still matter. Automation should narrow the decision space. There are real consequences to a wrong takedown request, especially when parody, commentary, resellers, and legitimate affiliates get involved.
Good CTI automation builds guardrails. It tags “likely unauthorized” versus “needs review.” It routes ambiguous cases to humans. It logs decisions and evidence so you can defend your actions later. That’s how you get speed without becoming reckless.
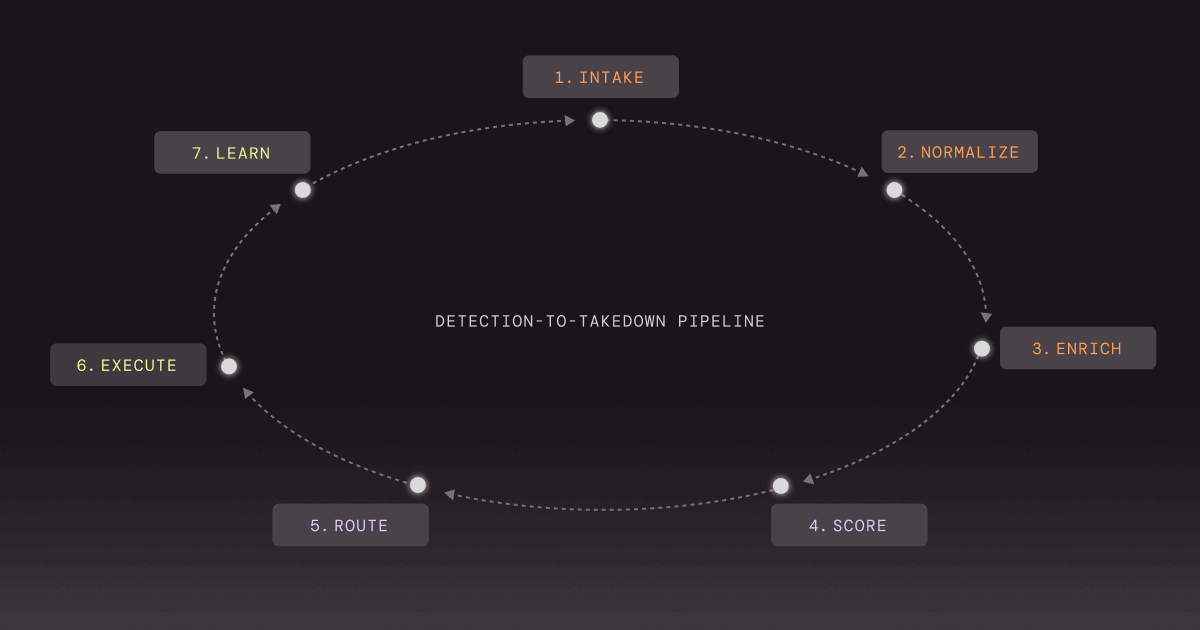
How Do You Build a Detection-to-Takedown Pipeline That Works?
You build it like an operational system, not a research function. Intake. Normalize. Enrich. Score. Route. Execute. Learn. Then you do it again, faster. The difference between “intel” and “operations” is whether the output is a decision that triggers action.
A working pipeline also has ownership. Someone owns intake quality, someone owns scoring logic, someone owns takedown execution, and someone owns feedback loops. Without ownership, everything becomes “shared,” and shared sometimes means neglected.
Start With a Clear Definition of Actionable
Actionable means the signal includes enough evidence and context that someone can confidently execute a response. That response might be takedown, escalation, threat monitoring, or customer-facing mitigation. The key is that the next step is obvious and supported by proof.
An actionable brand fraud alert typically includes: the asset, what it’s doing, how it’s targeting victims, the brand elements it’s abusing, and supporting artifacts such as screenshots, redirect chains, page HTML captures, timestamps, and platform identifiers. If you can’t answer those questions quickly, your responders will do the work themselves, which defeats the point.
Use Scoring That Matches Business Impact
Scoring should reflect what actually hurts you, not what looks dramatic in a screenshot. Credential theft, payment diversion, fake support channels, executive impersonation, counterfeit sales, and unauthorized apps are not equal. Treat them like they are, and you will waste time.
A practical scoring model ties risk to two things: expected harm and expected exposure. Harm occurs when someone engages. Exposure is how many people will encounter it and how fast it spreads. Then you add confidence. If confidence is low, the system should push it to review rather than execution.
What Signals Matter Most for Brand Fraud CTI?
The best signals show attacker preparation and attacker distribution. Catching the final phishing page is useful, but it is late-stage. Earlier signals often look boring until they’re not. If you want to get ahead consistently, you need signals that help you see the campaign before it peaks.
You also need signals that connect channels. A domain alone is one problem. A domain tied to a social account, which is tied to a paid ad, which is tied to a fake support number, is a campaign. Campaign-level visibility is where CTI automation earns its keep.
Domain and DNS Signals
Lookalike registrations, certificate issuance, DNS changes, and shared hosting patterns often reveal campaign clusters. Domains are still the backbone of a lot of brand abuse, even when the customer entry point is an ad or a social post. This is why external scam website monitoring remains a core input into CTI automation, because the final destination usually needs somewhere to land.
What to watch beyond basic typos: sudden bursts of registrations, naming patterns that mirror your product lines, suspicious TLD choices, short-lived hosting, and infrastructure reuse across lookalikes. The more you can automatically correlate those patterns, the faster you can treat a cluster as one operation instead of twenty separate tickets.
Social and Messaging Signals
Impersonation accounts move quickly across platforms and naming conventions, and they are often used as trust accelerators. A convincing social profile can push victims to click a link or call a phone number before they ever see a domain.
What tends to matter: profile naming patterns, repeated bios, reused imagery, and the relationship between a social account and its destination infrastructure. If CTI automation can connect the “front door” account to the backend landing pages and payment endpoints, your response can target the campaign rather than just the surface.
Paid Ad and Search Abuse Signals
Malicious ads and sponsored listings can scale exposure in minutes, and ad creatives rotate constantly to evade review. If you are not watching distribution channels, you’re always arriving late. Paid search abuse also creates a perception problem. Customers assume the top result is safe. Attackers exploit that assumption.
CTI automation helps by capturing ad variants, resolving destination URLs, tracking changes to redirects over time, and correlating creatives back to the infrastructure. It also helps you prioritize, because paid distribution often indicates intent to scale.
App Store and Marketplace Signals
Unauthorized apps and counterfeit listings are high-friction to remediate if you wait until customers complain. App ecosystems add another layer of complexity because the asset is not just a page, but a package, a developer identity, a permissions set, and an update pipeline.
Signals that matter include: developer account patterns, cloned UI flows, suspicious permission requests, and links inside the app that route to known bad infrastructure. In marketplaces, watch for seller networks, listing reuse, and content fingerprints that repeat across brands.
How Do You Enrich CTI Signals without Creating More Noise?
You enrich by answering the questions your responders will ask anyway. What is it? Who is it targeting? How is it spreading? What is the evidence? What is the recommended action? Enrichment that does not reduce responder work is just more data.
The goal is to convert “something weird” into “a ready-to-run case.” That means you enrich for decisioning and for takedown success.
In short, enrichment is only “good” if it makes takedowns faster and more successful.
Enrichment That Actually Helps
Here is the enrichment that tends to move the needle.
- Screenshot capture and page render history, with timestamps
- Redirect chain resolution, including intermediate hops and final landing
- Brand element matching. logos, copy, product names, support language
- Credential capture indicators. login forms, MFA prompts, account recovery bait
- Payment diversion indicators. invoices, wire instructions, crypto wallets
- Infrastructure context. hosting, registrar, certificates, shared IP space
- Platform identifiers. account IDs, ad IDs, app package names, seller IDs
Notice what is missing. A long list of external feeds. Feeds can help, but if your evidence packet is weak, takedowns fail, and responders lose trust in automation.
Correlation Beats Volume
One high-confidence campaign view beats 200 single indicators. When multiple signals point to the same operator or infrastructure cluster, your response becomes faster and more strategic.
Correlation also improves prioritization. If a new domain appears and shares infrastructure with a known credential theft campaign, you can immediately score it higher. That’s how CTI automation stops being reactive. It starts enabling earlier, higher-confidence intervention.
How Do You Prioritize What Gets Taken Down First?
You prioritize by impact and exposure. A convincing fake support account targeting high-value customers can be worse than a sloppy phishing site with no traffic. Prioritization is where most programs quietly fail because the scoring model is either too simplistic or too detached from customer harm.
A strong system also prioritizes by removability. If you can quickly knock out a distribution channel, you reduce exposure even if the landing site remains live for a bit. That is a tactical choice, not a moral one.
Use a Simple Priority Model
A practical model uses four factors:
- Impact: What happens if a victim engages? Credential theft, payment diversion, PII harvesting, account takeover, counterfeit purchase.
- Exposure: How many people will see it and how quickly? Paid ads and viral posts score high.
- Confidence: How sure are you that it’s malicious or unauthorized?
- Effort: How quickly can you remove it, and what dependencies does it have?
Then you apply guardrails. Some things always go to the top, such as active credential theft targeting customers. Some things always require review, such as borderline trademark use or possible parody.
Make Customer Harm a First-Class Signal
If the asset is designed to steal credentials, divert payments, or harvest PII, it goes to the top. You also want to factor in brand-specific risk. A bank, a retailer, and a SaaS platform will see different fraud outcomes. The scoring model should reflect reality, not a generic rubric.
How Does Automated Takedown Work without Creating Risk?
Automated takedown works by combining policy guardrails with repeatable evidence packaging. You don’t want a system that blindly fires off requests. The goal is repeatable, platform-appropriate submissions for high-confidence abuse, plus a review path for ambiguity.
Most takedown programs don’t fail because the asset is bad, but rather because the request isn't aligned with the platform’s process or because the evidence is incomplete. Automation can fix that by standardizing the evidence packet every time.
Evidence Packaging Matters
Takedowns fail when evidence is incomplete, inconsistent, or not aligned to the platform’s rules. Automation helps you package evidence in the format that succeeds. In some cases, that means routing high-confidence impersonation through a DMCA takedown workflow when copied assets are central to the abuse. Screenshots with timestamps. URL and redirect history. Proof of brand impersonation. Proof of customer harm risk. Platform identifiers.
It also helps you preserve artifacts for later enforcement. If the same actor reappears, you can show a pattern rather than just a single incident. Pattern evidence is often what leads to faster action in repeat-offender situations.
Guardrails You Should Require
Guardrails keep automation from becoming reckless and help you explain your program internally. If you’re going to automate execution, require guardrails.
- Approved asset lists for your owned domains and official accounts
- Category rules: phishing vs counterfeit vs impersonation vs affiliate misuse
- Review queues for ambiguity, such as parody or commentary
- Escalation paths for executives, regulated regions, and high-value customers
- Rate limits and approval gates for new platforms or new takedown types
- Audit logs that capture evidence, decision-making, and actions taken
What Should You Measure to Prove CTI Automation Is Working?
You measure operational outcomes, not the number of indicators you collected. The dashboard should tell you whether customers are safer and whether your team is spending less time chasing repeat campaigns. If you only measure volume, you’ll end up optimizing for volume. That‘s how teams end up “winning” by generating more alerts while brand abuse stays steady.
Metrics That Matter
Here are the metrics that tend to reflect real progress:
- Time to detection and time to takedown, segmented by channel
- Percent of high-risk assets removed within SLA
- Repeat rate, meaning how often the same campaign reappears under new assets
- Re-entry interval, meaning how quickly a campaign regenerates after takedown
- Analyst time per resolved case, including review and evidence packaging
- Coverage across channels, such as domains, social, ads, apps, and marketplaces
- Success rate by platform, including failure reasons and re-submit cycles
If you can tie these metrics to reduced fraud loss, lower support ticket volume, or fewer customer complaints, you will have an easier time getting budget.
Watch for Automation Theater
If your CTI automation produces a beautiful queue but doesn’t reduce incident recurrence, it is not automation.
A quick test. Pick ten high-risk takedowns from last month. How many were detected early, packaged cleanly, executed quickly, and tracked to closure without manual scrambling? If the answer is “not many,” the problem is usually workflow integration.
Where Do Most CTI Automation Programs Go Sideways?
They usually fail in predictable ways. Too many inputs, not enough decision logic. Or they automate collection and stop right before execution. The result is a mountain of “intel” with no operational endpoint.
Failure also happens when teams treat CTI automation as a one-time implementation. Attackers adapt. Platforms change. Your scoring logic and evidence templates have to evolve, or the system degrades quietly.
Over-Indexing on Feeds
Feeds are easy to buy and easy to integrate. They’re also easy to ignore. If your intel doesn’t route into action, it won’t change outcomes. In brand protection, higher leverage often means better correlation and better evidence packaging. You want fewer, higher-confidence signals that map to response actions.
Not Closing the Loop
Your takedown outcomes should feed back into scoring, correlation, and playbooks. If a specific host, registrar, naming pattern, or creative template keeps recurring, your system should get faster at spotting it.
Closing the loop also means capturing what didn’t work. Which platforms rejected requests? Which evidence elements were missing? Which categories require legal review? That feedback is how you reduce friction over time.
Key Takeaways
- CTI automation is only valuable when it turns signals into prioritized response actions.
- The best brand fraud intel reveals campaign relationships, not isolated indicators.
- Automated takedowns need guardrails, standardized evidence, and exception handling.
- Measure outcomes, such as time to takedown and repeat rate, rather than indicator volume.
Want CTI Automation That Reduces Brand Fraud Instead of Just Reporting It?
If your team is stuck triaging impersonation alerts and manually assembling takedown evidence, you don’t need more noise. You need a detection-to-takedown workflow that runs like a system.
That is what our platform is built to do. We automate discovery across the channels attackers use, correlate signals into campaigns, and drive takedowns with consistent evidence and human oversight for edge cases.
If you want to see what this looks like against your real abuse patterns, talk with us. We will walk through a live example and show where automation will save time, reduce re-entry, and remove more assets that actually harm customers.