In recent research, Doppel’s Threat Intelligence Team uncovered a long-standing bug affecting some Drupal Webform implementations that lets files be uploaded without submitting the form.
Attackers are abusing it to plant scam PDFs on trusted domains, including .edu and .org, which are then indexed by search engines. Together with forum abuse, this tactic makes scams look official and increases the odds that victims will call fake support numbers or click malicious links.
The file-upload bug
Drupal’s issue tracker documents a Webform behavior reported as early as 2021: files can be uploaded to the server without a completed submission. When sites store those uploads in the public file system, the files are accessible under paths like /sites/default/files/webform/, which search engines can crawl unless you explicitly block indexing. Drupal’s own documentation warns against enabling public, anonymous uploads for exactly this reason.
The result is a low-effort abuse path: plant a scam PDF on a trusted website and let search do the distribution.
Real-world abuse
During our investigation, we saw this exploited in multiple ways:
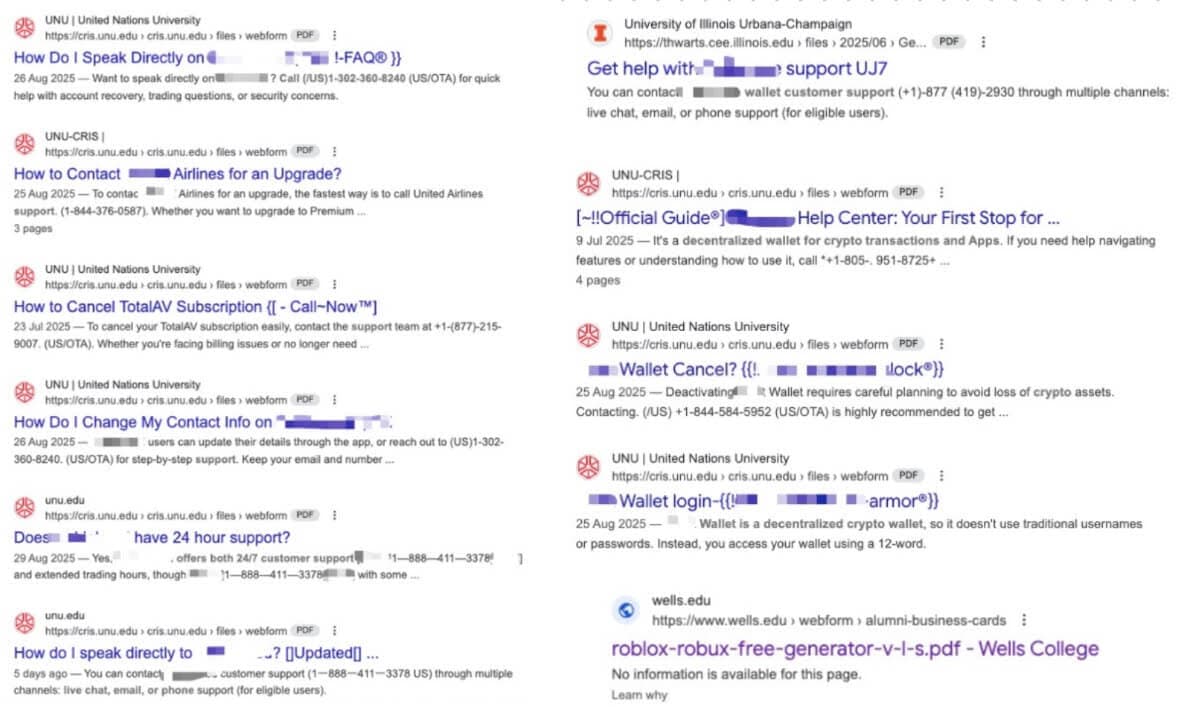
Scam PDFs impersonating airlines with fake “customer service” numbers.

Crypto-focused PDFs pushing fraudulent recovery hotlines.

- Forum posts on public support boards (including WordPress.org threads and community forums) seeded with “official contact number” topics that list scam phone numbers and URLs.

In some cases, the file or its links redirect from the trusted site to an external landing page, adding another layer of deception. Even after site owners remove the uploads or posts, cached search results may keep the scam snippets visible for a period of time, which prolongs the risk.
Threat actors are not limited to benign PDFs. The same path could deliver malware disguised as help documentation or account-recovery instructions. A user who trusts the domain may download it without hesitation.
How we verified it
To validate the technique, Doppel’s Threat Intel Team replicated attacker behavior on a domain we identified via search:
- Identified a vulnerable webform.
- Created a clearly labeled, harmless test PDF: “Security Test File – No Action Needed.”
- Explained in the document that this was a security test and that attackers abuse the bug to publish fake support numbers.
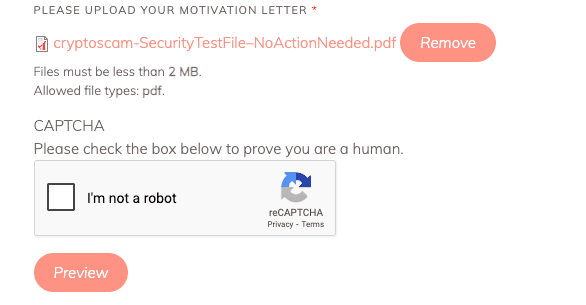
- Uploaded the file without submitting the form.
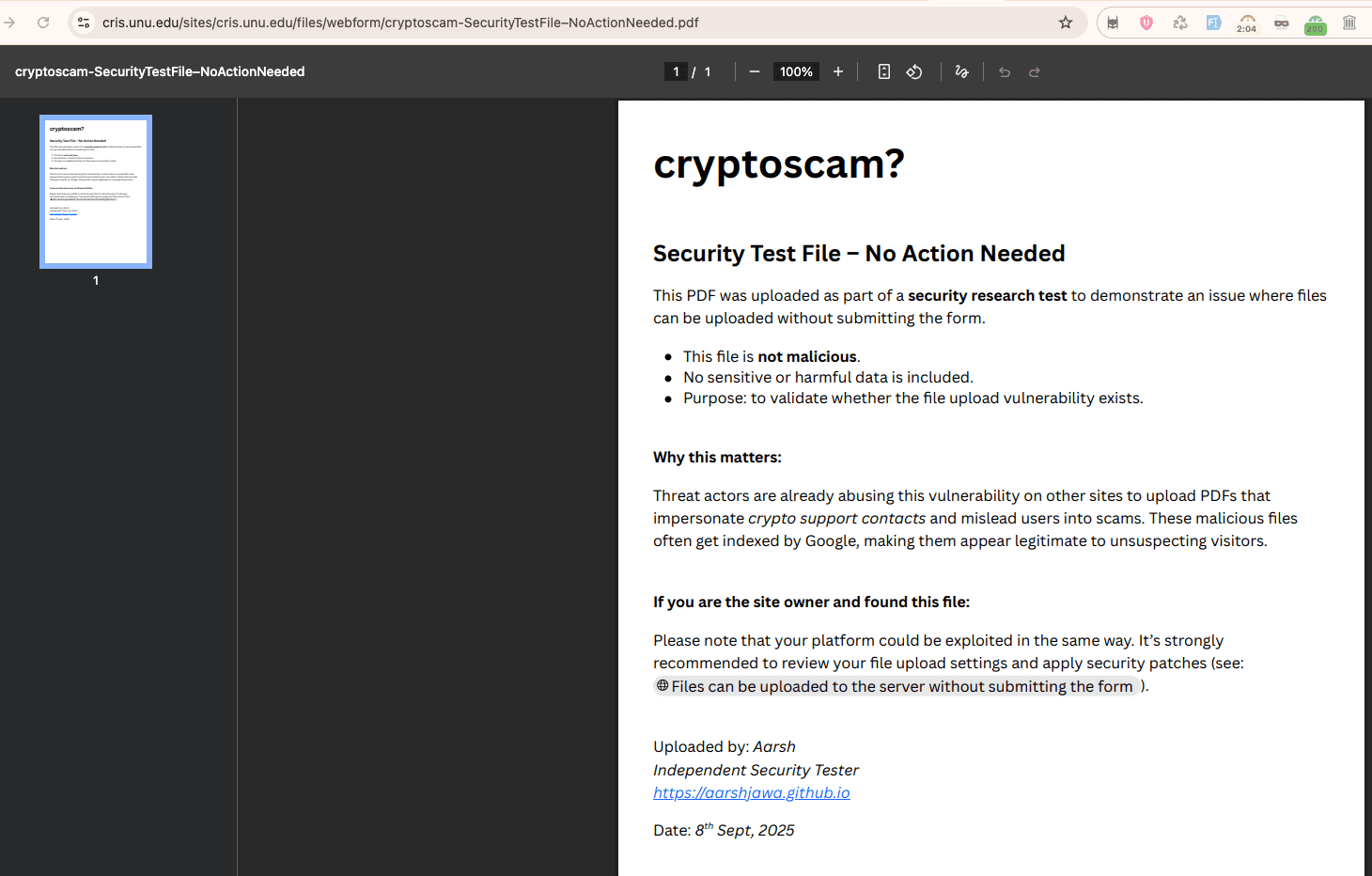
- Verified that the file was immediately reachable in the site’s public webform directory.
Test file (for reference):
https://cris.unu.edu/sites/cris.unu.edu/files/webform/cryptoscam-SecurityTestFile%E2%80%93NoActionNeeded.pdf
As with attacker uploads, a file in a public directory will eventually be indexed unless site owners block it.
Why this matters
- Brand abuse: Universities, nonprofits, and forums risk reputational damage when their domains host scam content.
- User risk: Seeing a phone number or “support” document under a .edu, .org, or reputable forum confers legitimacy and drives calls and clicks.
- Malware delivery: The same mechanism can deliver malicious payloads under the guise of help files.
- Persistence: Removal is not the end. Cached search snippets can keep bad numbers and messages visible for a while.
What to do now
This is a classic example of a “small” flaw that scales. Treat it with production discipline:
- Tighten file-upload controls. Require full form submission before persisting files. Disable public, anonymous uploads where possible.
- Audit your storage. Regularly scan and clean
/sites/default/files/webform/or equivalent public paths. - Constrain indexing. Use
robots.txtand meta directives to limit crawling of upload directories, and request cache removals when you take down scam files. - Harden forums. Increase moderation for “support number” threads. Use keyword and link filters. Enforce rate limits and new-user review queues.
- Instrument visibility. Log file-upload events and alert on spikes, unusual MIME types, or known scam patterns.
- Train your team. Make sure support, comms, and IT know how to spot and escalate fake contact-center content quickly.
How Doppel can help
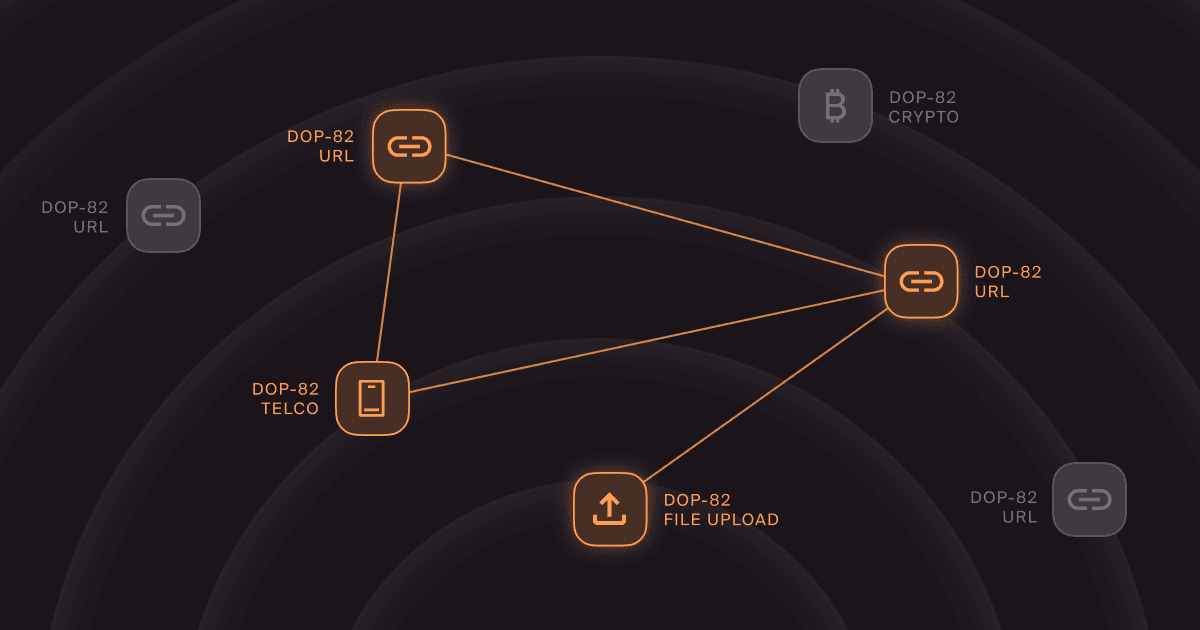
Doppel is built to detect and dismantle multi-channel scams that mix web uploads, search manipulation, social posts, messaging apps, and number-based lures. Our real-time threat graph links domains, accounts, ads, wallets, and phone numbers into a single campaign view so you can disrupt infrastructure, not just artifacts.
We also bring telco-aware defense to the problem. Doppel correlates phone numbers and short codes used in fake “support” operations, enriches them with cross-channel evidence, and streamlines disruption with the right providers. That means faster identification of scam hotlines, fewer repeat abuses, and coordinated takedowns across registrars, platforms, and carriers.
If you are seeing scam PDFs, fake support threads, or suspicious contact numbers tied to your brand, Doppel can help you see the full campaign and cut it off at the source. Request a demo to see how the Threat Graph and telco coverage work together to protect your users and your reputation.