Telecommunications fraud is costing companies billions of dollars and has put a serious damper on business operations worldwide. From smishing to Wangiri fraud, cybercriminals are upping their antics and making threats more difficult to detect and prevent. Beyond financial and operational damage, telecom fraud can strain customer trust and weaken the overall security of telecom networks.
Traditional fraud detection methods often fall short, relying on reactive approaches that fail to keep up with sophisticated fraud schemes. To effectively combat this threat, businesses must adopt proactive, AI-driven fraud prevention strategies that can identify and mitigate risks in real-time. By leveraging advanced technologies, organizations can protect their networks, safeguard revenues, and maintain the integrity of their telecom services.
What Is Telecommunications Fraud?
Telecommunications fraud is an unauthorized or deceptive activity that exploits telecom networks, services, or billing systems for financial gain. Malicious actors often manipulate phone systems, compromise accounts, and take advantage of security vulnerabilities for fraudulent gain at the expense of businesses and consumers. This type of fraud affects mobile operators, VoIP providers, and enterprises that rely on telecom services.
In 2024, the Global Anti-Scam Alliance (GASA) estimated over $1.03 trillion in losses globally due to fraud in just the past year, with phone calls and text messages remaining the primary methods of initial contact. Sadly, only 4% of the scam victims worldwide reported any recovery from their losses.
On top of financial losses, organizations endure operational disruptions, reputational damage, and regulatory and compliance risks, including legal and compliance penalties.
Common Types of Telecom Fraud Businesses Face
Organizations are under attack constantly with all types of social engineering attacks, but today we’ll focus solely on the common types of telecom fraud.
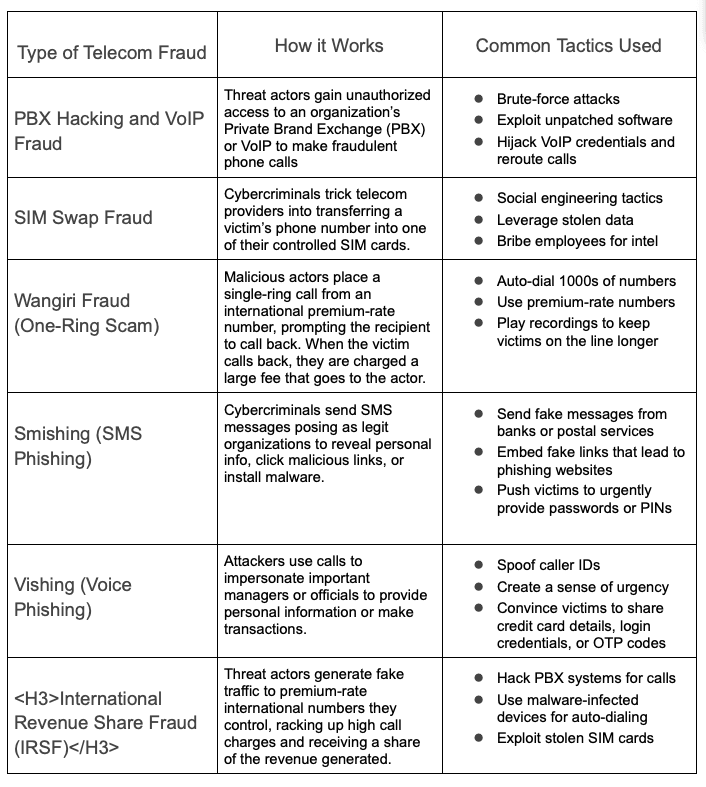
All these types of telecom fraud threaten organizations worldwide, but once organizations understand how this particular fraud works, they can more easily protect their business and prevent social engineering attacks.
Why Traditional Fraud Prevention Measures Are Falling Short
Knowing about the latest scams is one thing, but implementing effective fraud detection in telecommunication is another thing. Traditional fraud detection methods may not cut it as they often rely on reactive approaches that only detect telecom fraud after it’s occurred. If organizations wait until suspicious activity alerts, malicious actors may already be in their systems and networks wreaking havoc, gathering intel, or causing significant damage to their finances and operations.
The Business Research Company found that AI in the fraud management market was $13.05 billion in 2024 and is expected to grow to $15.64 billion in 2025. This increase is attributed to an increase in cyber threats, data breaches, the cost of fraud, and an increase in transactions.
As cyber criminals up the ante with AI-generated robocalls, SIM swap fraud, and PBX hacking, it’s time for organizations to beef up their cybersecurity systems with more advanced and proactive solutions to strengthen their defenses.
How to Effectively Protect Your Business from Telecom Fraud
Implementing security best practices can help businesses detect, prevent, and mitigate fraudulent activities before exploitation. Below are some proven strategies organizations can take to strengthen their fraud prevention efforts.
1. Strengthen Security Protocols
Hardening security protocols is essential to protecting telecom networks from unauthorized access and fraud. By enforcing multi-factor authentication (MFA), organizations can prevent cybercriminals from gaining control over accounts and systems. Businesses should also restrict international dialing and disable unused services to reduce vulnerabilities and security gaps that could lead to PBX and VoIP exploitations. Organizations should also add encryption and firewalls to protect sensitive telecom infrastructure.
2. Implement Real-Time Monitoring and Alerts
Real-time monitoring and automated alerts are critical for early detection. Through advanced AI-driven fraud detection systems, organizations can automatically analyze call patterns, find anomalies, and block suspicious activity. Businesses should leverage brand protection solutions and set up customized fraud detection rules, such as limits on call durations, high-cost destinations, or unusual traffic spikes to identify potential threats.
3. Conduct Regular Security Audits and System Updates
Telecom fraud often stems from the exploitation of outdated software, misconfigured settings, or unpatched vulnerabilities. Through regular security audits, businesses can assess potential weaknesses in PBX, VoIP systems, and network security settings. Telecom security managers should set up routine software updates and patch management programs with penetration testing and vulnerability assessments to identify security gaps before exploitation.
4. Educate Employees and Promote Awareness
One constant flaw in security is humans. Organizations should ensure employees receive security awareness training and education on common social engineering and fraud tactics. Security awareness programs should include guidelines for handling sensitive telecom credentials, verifying callers, and reporting fraud attempts. Organizations should encourage a culture of awareness and openness to report suspicious activities so their entire team is ready, aware, and prepared.
By implementing these proven fraud prevention strategies, businesses can enhance their telecom security, detect threats in real time, and minimize financial losses.
Doppel’s Telco Module: A Powerful Tool Against Telecom Fraud
If you’re looking for an advanced telecom fraud detection and prevention platform, explore Doppel’s Telco Module. Our telco module helps businesses combat telecom fraud with proactive protection by removing fraudulent phone numbers in real time, reducing fraud-related losses, and minimizing disruption.
Get real-time monitoring using advanced AI to identify and mitigate fraud before it impacts your business.


