This week, a high-severity NPM supply-chain attack briefly compromised several of the most widely used JavaScript packages, collectively racking up over 2 billion weekly downloads.
Though its actual impact appears limited, the incident underscores the inherent risk posed by widely trusted libraries. This also brings us back to the burning question, how do you strengthen your first line of defense, employees and customers, against these types of social engineering attacks?
At Doppel, we took the NPM attack as an opportunity to help security teams, employees and customers better-equip themselves with the ability to identify these kinds of attacks.
Doppel Simulation gives security leaders an easy way to test their employees' defenses against the latest, real-world threats in just a few clicks. Security teams can enter natural language prompts to generate phishing simulations that safely replicate attacks that are consuming media headlines. This gives them real-time data on how their organization would fare when faced with a similar threat, and an opportunity to effectively train employees on how to protect themselves.
Here’s what we came up with using Doppel Simulation to build an effective simulation of the NPM attack:
The NPM Attack Story: What Happened?
On September 8, 2025, at approximately 9 AM EST, attackers successfully social-engineered access to a maintainer’s NPM account, notably the developer behind packages such as debug and chalk.
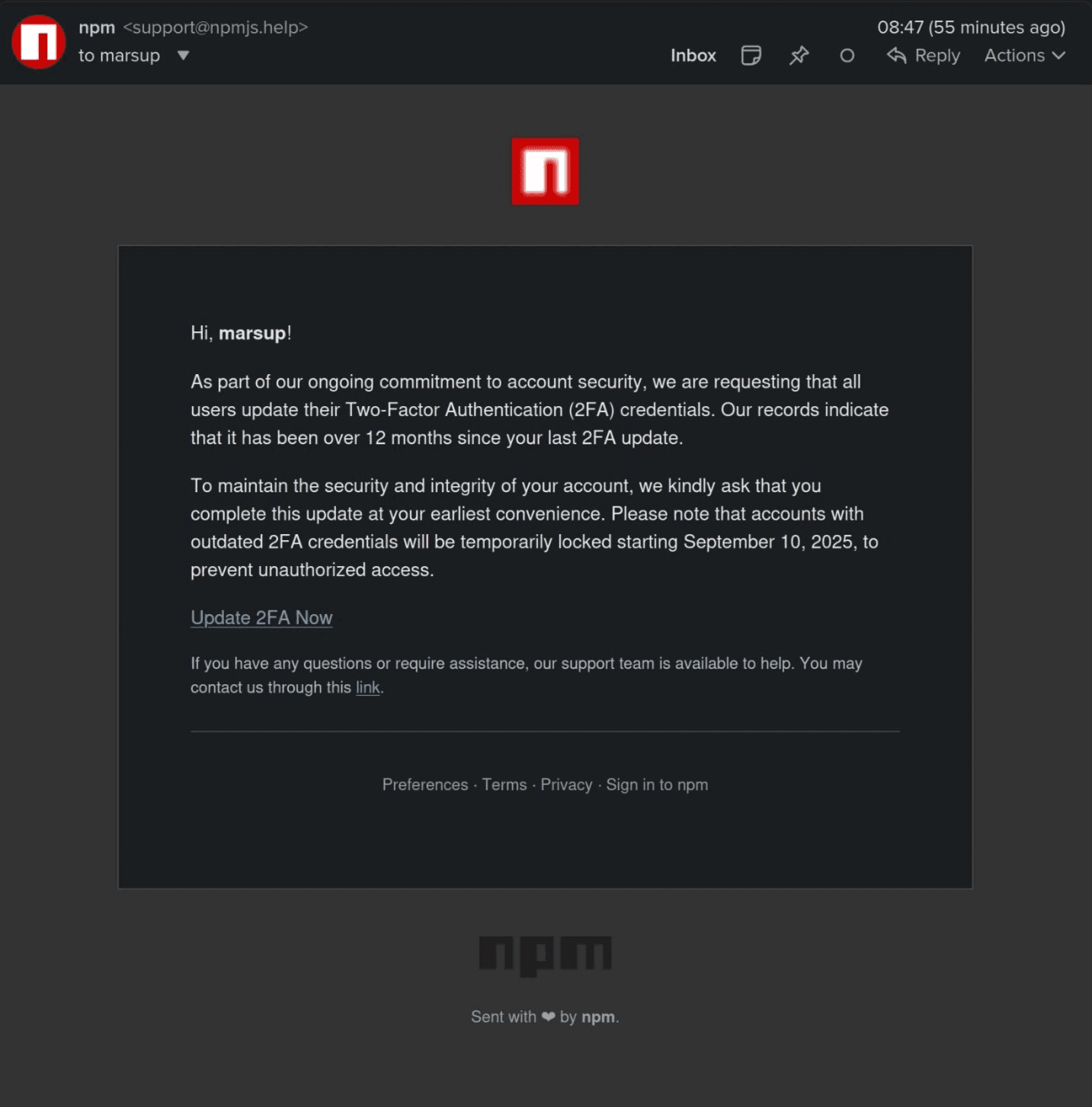
Within a two-hour window, compromised packages were published as new malicious versions containing obfuscated browser-side interceptors. These payloads were designed to monitor cryptocurrency activity,hooking into browser APIs like fetch, XMLHttpRequest, window.ethereum, Solana and others, and silently rewrite wallet destinations or approval flows so crypto assets routed to attacker-controlled accounts.
According to Bleeping Computer, the packages affected included an extensive list, such as:
- debug (357 million weekly downloads)
- chalk (300 million)
- ansi-styles (371 million)
- strip-ansi, supports-color, ansi-regex, wrap-ansi, color-convert, color-name, color-string, and others—all totaling more than 2 billion downloads per week.
Wiz researchers measured impact: 99% of cloud environments used at least one compromised package, and up to 10% of environments actually incorporated the malicious code during that two-hour period.
However, reports suggest that actual cryptocurrency theft was minimal, as the malicious code lacked persistence and telemetry, rendering the attack more of an operational burden than a financially devastating one.
Why The NPM Attack Matters
a. Supply-chain risks in real time
Supply chains have rapidly become one of the most sensitive pieces of a company’s defenses. The incident underscores the importance of extending security control and defenses to every link in the supply chain.
b. Velocity of security incidents
This incident spotlights how even fleeting attacker control, just a couple of hours, can ripple rapidly through CI/CD pipelines, build systems, and browser-served applications. The web’s dependence on transitively included libraries meant damage spread in minutes, not days.
c. The effectiveness of social engineering
Perhaps the most alarming piece of the NPM puzzle is the fact that a relatively unsophisticated attacker was able to gain access to packages accessed by billions of users through a 2FA phishing email underlines the potency of these types of attacks.
What This Means for Security Teams
Security breaches like the attack on NPM result in a flurry of news and media coverage that can leave security leaders with the burning question: How do I make sure that my organization isn’t in the headlines next?
Protecting against this type of attack is paramount in an age where social engineering threats are more prevalent and sophisticated than ever. Threat actors are gathering intelligence on users, teams, and companies to create extremely personalized and believable scams that trick even savvy teams.
In order to keep pace with attackers, security leaders are turning to tactics that test, train, and strengthen their defenses against even the most sophisticated attacks–which starts with effective simulations.
Doppel provides dynamic, multi-channel phishing simulations that offer a safe, thorough approach to security training. AI-powered recon emulates threat actor behaviors to create simulations tailored to a user, team, or company based on real-world intel and threats. Security teams can even clone threats detected by Doppel’s Brand and Executive Protection products, testing their employees’ responses to actual threats in a secure environment. The platform also generates quizzes and training prompts, personalized based on a user’s behavior or role to effectively educate without being punitive.
A strong simulation program helps security teams take swift action during periods when uncertainty and fear is driving the narrative. Ultimately, Doppel Simulation gives security teams the toolkit to build a training program that bolsters their defenses and effectively reduces risk.
Final Thoughts
This week’s NPM breach was brief but potent — a live demonstration of how attacker-injected payloads in trusted libraries can turn a few minutes into widespread risk. The fortunate outcome: minimal theft but maximum wake-up call.
For developers and security teams, this incident reiterates an enduring lesson: trust no package implicitly. Effective attack simulation is the best way to prepare your team. In an ecosystem built on open collaboration, vigilance is every organization’s most effective safeguard.
To increase the resiliency of your organization, try Doppel Simulation.
Attend our simulation webinar on September 16th! Register here.