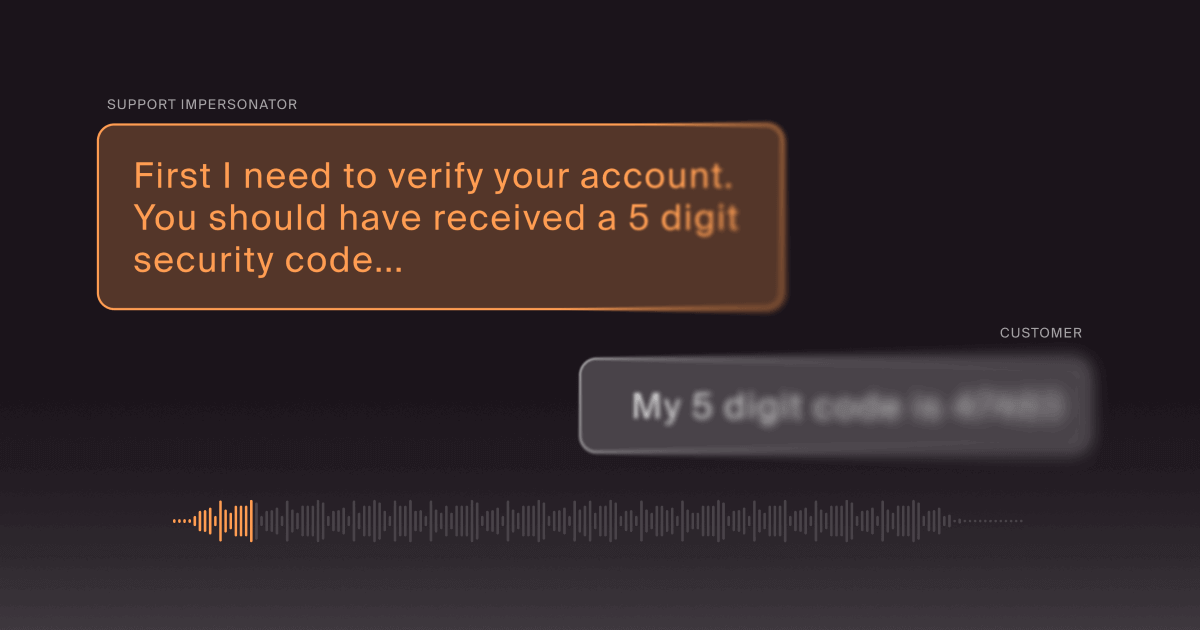
Vishing brand impersonation is a phone-based social engineering attack, a version of a scam that already works way too well. Someone calls pretending to be your brand, your support desk, or a “trusted partner,” then tries to steer the victim into giving up what actually matters. One-time passcodes. Login credentials. Payment details. And it is rarely just a random robocall. The call usually has backup. A believable script, a spoofed caller ID, and often a fake “support” page or lookalike site that makes the whole thing feel official.
People will delete a suspicious email in two seconds. Put a calm voice on the phone, add a little urgency, and suddenly smart people start reading out one-time passcodes like they are ordering coffee. That is the core problem with vishing brand impersonation. The attacker is not just calling. They are borrowing your brand’s authority to make the scam feel legitimate in real time.
When we talk with security, fraud, and customer care teams about vishing, we frame it as an impersonation attack surface issue. The phone call is often the closing move in a larger, multi-channel campaign that also includes lookalike sites, fake support numbers, and text messages. The pattern we see a lot looks like this: Someone searches “{Brand} customer support,” finds a page with a “support number,” calls it, and the “agent” immediately pivots to “verification,” meaning they want the one-time passcode you just received.
Why Vishing Brand Impersonation Is Surging
Vishing is not new. What has changed is the speed and scale. Attackers now combine stolen customer data, cheap calling infrastructure, and AI-generated voice to make calls feel personal, credible, and time-sensitive.
Instead of a single scammer dialing one victim at a time, many campaigns run like a small call center. They rotate numbers, reuse scripts, and pivot channels until someone bites. Your brand name is the trust multiplier that makes it work.
Why Trust and Urgency Make Vishing Brand Impersonation Work
People still trust a live phone call more than an email or an ad. That instinct is exactly what vishing brand impersonation exploits.
In practice, these campaigns thrive when the phone channel is outside formal security monitoring, and attackers can anchor their scripts to something that sounds plausible, like a recent purchase, a password reset, or an open support ticket. Then they add the special ingredient: urgency. “Your account will be locked in ten minutes unless you verify this charge” is basically the attacker’s love language.
If you don’t have visibility into how your brand is being used across voice and the surrounding infrastructure, you end up finding out the hard way, after losses, angry customers, or regulator complaints land on your desk. And yes, it can turn into a real incident fast. The FBI has issued recent public warnings about criminals impersonating financial institutions to enable account-takeover-style fraud. The exact brand varies, but the mechanics are the same: authority, urgency, and a request that hands them the keys.
AI Voice and Spoofed Numbers at Scale
Generative AI has lowered the barrier to creating realistic synthetic voices and convincing speech that sounds like a real employee or executive. This is not hypothetical anymore. The FBI has warned about campaigns using AI-generated voices to impersonate senior officials, paired with messages that push targets onto a “new platform” that turns out to be a credential-harvesting trap.
At the same time, telecom abuse services make it easier to operationalize attacks at scale. Attackers can spin up disposable VoIP numbers, spoof caller ID so the call appears to come from an official support line, and even build multi-step IVR flows that mimic real phone trees. In the U.S., illegal spoofing can trigger FCC enforcement, and STIR/SHAKEN helps authenticate caller ID, but real-world vishing still slips through because criminals route around trust signals and exploit gaps. The result is a wave of vishing brand impersonation that feels “legit” to victims. And that’s the whole point.
How Vishing Brand Impersonation Campaigns Actually Work
Behind each “one-off” vishing report, there’s usually a structured campaign. Attackers build the same infrastructure they use for web-based brand fraud, then attach a phone number and a script to it.
A Typical Vishing Brand Impersonation Playbook
A typical pattern looks like this:
- Set up fake touchpoints that feature your brand name, including lookalike sites, search results with fake “support numbers,” or forms that collect callback requests.
- Attach one or more phone numbers. These numbers are rotated frequently to evade blocking and reputation systems.
- Run targeted or broad outreach. Attackers call known customers, victims from previous data breaches, or random numbers, claiming to be fraud, billing, or tech support.
- Drive to high-value actions. They push victims to read out one-time passcodes, move funds, install remote access tools, or share card data. Sometimes they combine the phone call with a real-time login attempt, so the “verification code” the victim reads is the last step the attacker needs. (One version is “support” scams that talk the victim into installing a legitimate remote-help tool, then the attacker uses that foothold to escalate into something much uglier. Microsoft Threat Intelligence has documented real-world social engineering abuse of Quick Assist that led to ransomware activity.)
- Dispose and retool. Once a number is blocked or a domain is removed, the attackers replace it with a new one and restart the flow.
This playbook isn’t a single bad call. It’s an infrastructure problem tied to your brand.
Multi-Channel Infrastructure Behind a Simple Phone Call
The phone call is often the final step in a multi-channel workflow. We routinely see campaigns in which attackers plant fake support numbers in forums, comment sections, and file upload features so that those numbers surface in search results. Callback phishing is the cleanest example of this mash-up. The lure is “There’s a problem, call this number,” and the whole goal is to get the victim onto a voice channel where urgency and authority work better than links ever did.
If you want to stop vishing brand impersonation, you have to treat it as part of a larger impersonation ecosystem, not as isolated telecom spam.
Why Traditional Controls Miss Vishing Brand Impersonation
Unlike email phishing or SMS scams, vishing brand impersonation delivers the payload through a live conversation, where urgency, authority, and improvisation defeat static technical controls.
Most enterprise defenses still revolve around email, web gateways, and endpoint security. Those controls matter. They simply do not see or understand call-based impersonation on their own.
Email-Centric Defenses Do Not See Voice Attacks
Security stacks built around phishing tests and email filtering struggle when attackers pivot to the phone. There may be no URL to inspect or block. The payload is verbal, like a voice that sounds like an executive asking finance to move funds. And the attack can ride on top of a legitimate signal, like a real email followed by a fake phone call that references it, which is precisely why it works.
If your digital risk program only tracks domains and inbox threats, it may never connect the phone number that closes the loop.
Fragmented Signals Across Security, Fraud, and Customer Care
The clues that point to vishing brand impersonation are usually scattered across teams. Security might see credential stuffing tied to a new cluster of IPs, while fraud teams see chargebacks tied to “phone support” that does not match the official process. Meanwhile, the contact center hears customers complain about “the agent who called yesterday” from a number no one recognizes: same campaign, three inboxes, zero shared context.
When numbers, domains, content, and user reports live in different systems and teams, response stays reactive. That’s how repeat campaigns keep slipping through.
How to Detect and Disrupt Vishing Brand Impersonation
When we evaluate a vishing program, we look for two things. Coverage that is broad enough to catch the campaign, and a workflow that is fast enough to stop it. If either piece is missing, you end up with a neat spreadsheet of scam numbers and no actual reduction in customer harm.
Detection Signals That Matter
Effective detection isn’t just “monitor phone numbers.” It’s correlating numbers with the rest of the impersonation footprint.
- Phone number intelligence. Watch for numbers that appear near your brand name in search results, app listings, forums, and scam reports.
- Infrastructure correlation. Connect those numbers to lookalike domains, cloned support pages, and fake login flows.
- Content and script indicators. Track recurring phrases, verification prompts, and fake IVR patterns that mimic your customers' real journeys.
From Detection to Action
A response loop that works usually includes:
- Validation. Confirm the number, script, or destination is truly impersonation, not a customer misunderstanding.
- Containment. Block, report, and, where possible, remove the infrastructure that is driving victims to the phone channel.
- Customer messaging. Update help center guidance and IVR messaging so customers have a simple way to verify calls.
- Learning. Feed confirmed patterns back into monitoring, training, and fraud rules.
How Security and Fraud Teams Can Reduce Vishing Risk
Technology helps, but it’s not the whole answer. Vishing brand impersonation improves when teams share ownership and act quickly. Otherwise, the scam bounces between departments until it becomes “someone else’s problem,” which is a very expensive way to learn teamwork.
Build a Unified Vishing Playbook
Security, fraud, legal, and customer operations should share a single playbook for phone-based scams that touch your brand. At minimum, we want clear definitions that separate vishing brand impersonation from generic telecom spam, and a crisp triage flow for new reports from customers, regulators, or partners. We also want a single system to store canonical data on numbers, cases, and takedowns, because “it’s in three spreadsheets and a Slack thread” is not a strategy. Finally, set escalation triggers for law enforcement, telecom partners, or platform providers, so people are not making high-stakes calls based on vibes.
The strongest programs treat vishing as part of digital risk protection. They don’t treat it as a narrow contact center problem.
Prepare Employees and Customers with Realistic Training
Generic “watch out for phone scams” advice is no longer enough. People need to practice the same call patterns attackers use, including the awkward moment when the caller sounds completely reasonable.
We recommend three practical moves:
- Run simulations that mirror real vishing brand impersonation scenarios tied to your brand, partners, or executives.
- Give customer-facing teams short, consistent verification steps they can share with callers who feel pressured.
- Publish clear guidance on your site about how you will and will not contact customers by phone, including which numbers are official.
When training reflects reality, employees and customers are far more likely to pause, verify, and report suspicious calls early.
Where Doppel Fits. Connecting Vishing to the Bigger Impersonation Picture
At Doppel, we spend a lot of time treating vishing as one signal inside a broader brand impersonation campaign. That’s the heart of Social Engineering Defense. It’s not just finding “bad stuff,” it’s linking signals into a campaign and dismantling the infrastructure behind it. If you only chase the phone number, the attacker just swaps it and keeps going.
What You Get with Doppel’s Monitoring
In practice, we focus on three correlated views:
- Numbers near your brand. Clusters of phone numbers that show up alongside your brand name across the open web, marketplaces, and user-generated content, then get reinforced by complaints and blocklists.
- The web infrastructure that feeds the calls. Lookalike domains, cloned support pages, and fake workflows that push victims toward those numbers.
- The narrative. How scammers describe your process in scripts and posts, including fake IVR steps and “verification” prompts designed to extract passcodes or payments.
That correlation helps security, fraud, and brand teams see the campaign rather than just the latest number.
Key Takeaways
- Vishing brand impersonation is not just robocalls. It is a brand abuse campaign designed to create trust, urgency, and costly mistakes.
- Attackers use spoofed numbers, deepfake AI voice, and multi-channel infrastructure to make scam calls feel legitimate.
- Email and web controls rarely see voice attacks on their own. You need monitoring that connects phone numbers to domains, content, and victim reports.
- The fastest improvements come from shared ownership across security, fraud, and customer operations, plus realistic training and clear customer verification guidance.
- Vendor or no vendor, ask whether your program can spot the campaign, not just the phone number. That’s the difference between whack-a-mole and measurable risk reduction.
What’s the Next Practical Step for Stopping Vishing Brand Impersonation?
If you’re serious about reducing vishing brand impersonation, pick one concrete next step this week. Audit where your “official” phone numbers show up online, review the last 30 to 60 days of customer reports for patterns, and confirm you have a documented path for reporting and takedown when a fake number pops up. Then decide who owns it end-to-end, because attackers love nothing more than a handoff between teams.
If you’re ready to automate this process, take a look at how Doppel operationalizes campaign-level correlation and takedowns for impersonation-driven fraud, including vishing-adjacent infrastructure.