In the first quarter of 2025, the Anti-Phishing Working Group (APWG) observed over 1 million new phishing attacks. It’s a staggering assault on brand integrity.
Credential theft may have been the standard, but today’s brand impersonation phishing is a sophisticated strategy designed to exploit the trust you’ve poured resources into building.
When attackers impersonate your brand, they don’t just steal data. Attackers damage your reputation, erode customer trust, and cut directly into your revenue.
Brand phishing trends show that attackers are moving faster, using AI, and launching multi-channel campaigns that traditional defenses struggle to handle.
Let’s review the emerging phishing trends that allow attackers to exploit your brand. We’ll also explain why a modern, rapid-response framework isn’t optional and how you can shorten your response window from days to minutes.
Why Brand Impersonation Phishing Requires Immediate Attention
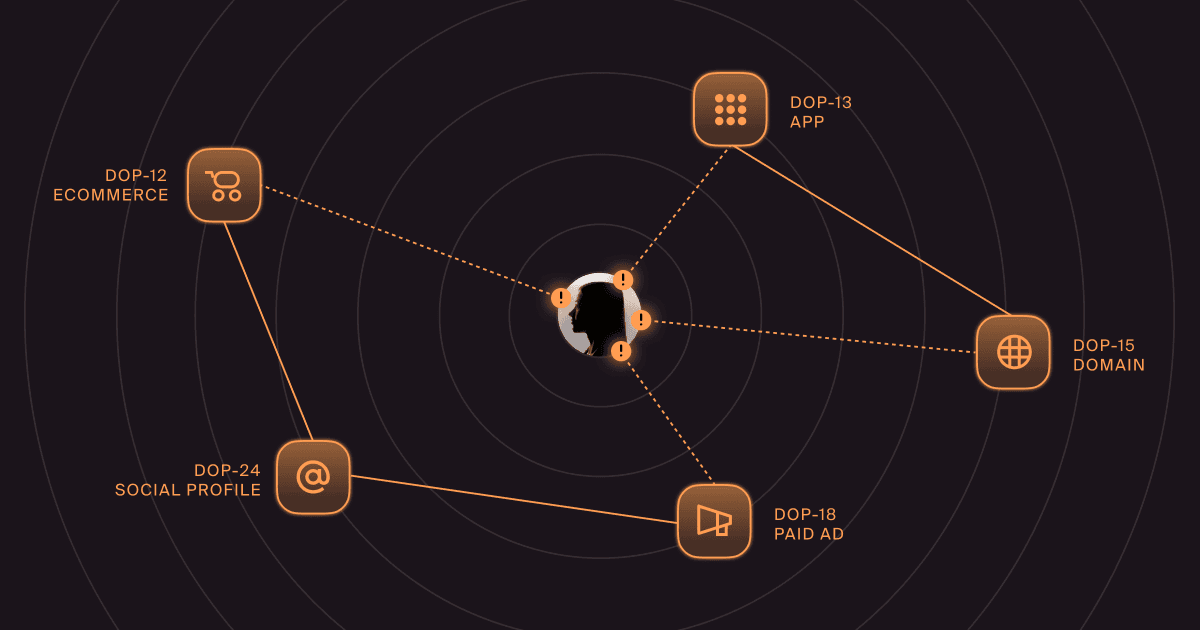
Brand impersonation phishing is an ecosystem of deception. It’s not just one fake email. It’s the combination of fake websites, cloned login pages, counterfeit social media profiles, malicious paid ads, and scam apps in official stores.
All these elements are designed to look and feel exactly like your brand, creating a convincing trap for your customers.
The scale is massive, and the business impact is severe. Imposter scams led to $2.9 billion in losses in 2024, and while those losses fell on U.S. consumers, it also meant lost revenue for businesses.
When an impersonator tricks customers, they don’t blame the scammer. They question the brand’s ability to protect them, and this leads to customer churn, loss of trust, and potential regulatory exposure.
The biggest challenge is that traditional security solutions can’t keep up. Your email gateway can’t see the fake social media profile, and your brand monitoring tool can’t see the malicious paid ad.
Attackers thrive in these silos, which is why we built our platform to focus on detecting and taking down entire impersonation campaigns rather than just isolated threats.
Emerging Brand Phishing Trends
Brand impersonation phishing is growing in frequency and evolving in sophistication. Attackers now exploit multiple digital channels at once, from domains and social media to malicious ads and mobile apps.
Here are the key trends our team is tracking.
The Ongoing Spoofing of Major Brands
Threat actors imitate well-known companies for one simple reason: Trust is a pre-built vulnerability. By masquerading as a brand that customers already recognize and trust, attackers dramatically increase their success rates.
Industries like technology, finance, and retail remain the primary targets. For years, Microsoft has been the most impersonated brand, used as a lure to steal corporate credentials.
Attackers use your recognizable logos, UI, and branding to create a false sense of security, tricking users into sharing sensitive data or payment details.
This is why our monitoring approach is designed to detect brand misuse before the first customer engages.
Lookalike Domains, Typosquatting, and Cross-Channel Impersonation
Today’s attackers are multi-channel and mutually reinforcing. It’s a coordinated operation.
A malicious paid ad impersonating your brand leads to a lookalike domain with a cloned login page, while a fake social media profile running your logo and brand colors links to a scam app in an app store.
These elements reinforce each other, making the scam far more believable and much harder for siloed security teams to track.
While your team is trying to take down one domain, the attacker is already driving traffic to it from three other channels.
Now you see why unified visibility is non-negotiable. We track these impersonations across domains, apps, and social platforms, linking disparate signals into a single, unified threat graph. It allows you to see the entire attack campaign, not just the individual pieces.
Faster, Smarter Phishing: AI & Automation
Generative AI and automation are to phishing what the assembly line was to manufacturing, enabling unprecedented quality, scale, and speed.
- Quality: Generative AI has eliminated the classic red flags. Typos, awkward phrasing, and grammatical errors are gone. AI now generates flawless, context-aware, and hyper-personalized messages at a scale that was previously impossible.
- Scale: Phishing kits and automation allow attackers to launch polymorphic campaigns, featuring thousands of unique variations of a single attack, in hours, all designed to evade traditional filters.
- New Vectors: Generative AI enables convincing, real-time voice (vishing) and video (deepfake) attacks. In one 2024 incident, a finance employee was tricked into transferring $25 million after a deepfake video call with people he believed to be his CFO and other colleagues.
You can’t find AI-driven attacks with manual human review. The speed mismatch is too significant, and that’s why we’ve built our platform on AI-assisted detection and automated workflow orchestration.
The only way to fight automation is with better, faster automation.
How to Respond Faster to Brand Impersonation Phishing
Recognizing these trends, the real advantage that you have is how quickly you can respond.
Every minute a phishing site, fake social media account, or malicious ad stays live, more customers are exposed. And the cost of slow action is astronomical.
According to IBM, the average time to detect and contain a breach is over 250 days. For brand phishing, that timeframe is a catastrophe.
Success depends on a rapid-response framework built on speed, visibility, and coordination. Here’s our process for closing the gap.
Step 1: Continuous Monitoring & Early Detection
Before the first customer ever sees a phishing link, the defense begins. You can’t take down what you can’t see, which is why continuous, 24/7 monitoring is the critical first step.
Full-spectrum brand monitoring must include domains, subdomains, social media, app stores, paid ads, and the dark web. Our unified platform provides this single-pane-of-glass visibility, ingesting and analyzing over 100 million indicators daily to identify brand misuse in real time.
Step 2: Rapid Takedown & Automated Enforcement
Detection is only effective if the takedown process is fast, reliable, and relentless. Identifying a threat and then taking three days to act is a failure.
Best-in-class response requires automation, direct coordination with registrars and hosts, and pre-built escalation workflows.
We combine AI-driven detection with human expertise to accelerate takedown coordination at machine speed, and the results are measurable:
- 4.82-minute median response time
- 30-minute median mitigation time for phishing URLs
- 24-48-hour median takedown time for domains, social media, and apps
The speed is what minimizes customer exposure and protects your brand from damage.
Step 3: Cross-Team Collaboration & Escalation Paths
Brand protection is an enterprise-level risk, not just a security or marketing problem, that can’t be handled in a silo. Your response requires clear coordination between security, brand, and legal teams.
You need escalation processes and ownership for every type of threat. Who handles a fake social media account? Who contacts the registrar for a lookalike domain? Who manages customer communications if a breach occurs?
These playbooks must be built before a crisis, so here’s your guide to a strong brand protection strategy.
Step 4: Post-Incident Review & Continuous Improvement
The goal is to anticipate and prepare for the next attack. Analyze attack patterns, campaign origins, and repeat offenders to move from a reactive ‘whack-a-mole’ approach to a proactive, predictive defense.
Our analytics and reporting capabilities are designed for this, revealing the long-term brand phishing trends targeting your organization. This intelligence, shared across departments, optimizes brand protection and strengthens your security posture.
The Bigger Picture: Staying Ahead of Brand Phishing Trends
The main takeaway is simple: As attackers accelerate, so must your defenses. Brand phishing is a high-speed, multi-channel threat powered by AI.
Defense requires a unified strategy built on three pillars:
- Complete Visibility: Seeing the entire campaign, not just isolated threats.
- Unmatched Speed: Automating the workflow from detection to takedown.
- Smart Collaboration: Partnering your security, brand, and legal teams.
We’re moving from an era of manual reaction to one of automated, predictive defense. It’s the new standard for protecting your customers, your revenue, and your brand.
Get a demo to see how Doppel protects your brand from phishing and impersonation threats.