What Is Data Loss Prevention?
Data loss prevention (DLP) is a layered approach that protects sensitive data from leaks and theft by utilizing policies, technology, and personnel to collaborate in preventing unauthorized access or sharing. It helps organizations protect customer data, intellectual property, and financial records, maintaining compliance and trust while reducing operational risk.
Data can be lost accidentally, through insider threats, or due to cyberattacks such as phishing. By utilizing DLP, companies can avoid regulatory fines, protect their reputation, and maintain customer trust while establishing a resilient security posture for a remote and cloud-driven world. Explore essential concepts of brand protection.
Why Data Loss Prevention Matters
DLP is essential for preventing disruptions, regulatory issues, and erosion of customer trust. The 2024 Verizon Data Breach Investigations Report found that phishing contributes to over 36% of breaches, showing how quickly data can be compromised.
Organizations face risks from misconfigured cloud storage, insider data theft, and accidental sharing. As companies shift to hybrid work and cloud-based tools, they must address these risks by exploring effective brand protection strategies that align with their data protection goals.
Core Components of a DLP Strategy
A DLP strategy combines technology, policies, and processes to locate sensitive data, enforce data handling policies, and monitor for violations, ensuring your organization is protected from leaks.
Core Features of an Effective DLP Strategy
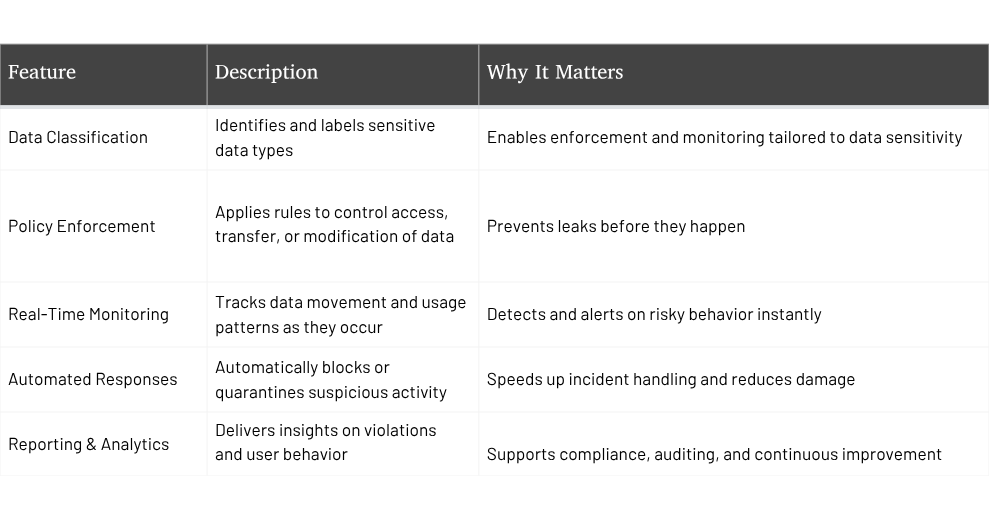
Data Identification and Classification
Data loss prevention begins with identifying and tagging sensitive data, including personal identifiers, payment information, and intellectual property, such as structured data in databases and unstructured data like emails, documents, and shared files. For example, an organization may classify customer SSNs, proprietary product designs, and confidential business contracts to ensure these assets are protected from accidental sharing or theft.
Policy Enforcement and Controls
Once sensitive data is identified, data loss prevention tools apply policies to control its movement and access, which involves blocking or quarantining data, encrypting files, or alerting security teams when policy violations occur. Context-aware controls allow policies to consider who is accessing the data, on what device, and from which location, ensuring data protection while maintaining user productivity. For example, a company can block large data downloads from unsecured devices or prevent sensitive files from being emailed to personal accounts.
Monitoring and Incident Response
Monitoring sensitive data in real time helps organizations detect suspicious activities, such as unusual data transfers, unauthorized uploads to cloud services, or sharing confidential documents outside the organization. With automated alerts and quick escalation procedures, security teams can respond rapidly to incidents, reducing the likelihood of breaches. For instance, if an employee attempts to upload customer data to an unsanctioned cloud platform, the system can automatically block the upload and notify the security team for follow-up.
Types of Data Loss Prevention Solutions
Organizations face different levels of data risk depending on their size, industry, and workflows. Choosing the right DLP solution depends on where your sensitive data lives, how it moves, and who accesses it. This section breaks down the main types of DLP solutions to help you evaluate which option best fits your environment, supporting your broader security and brand protection goals.
Types of DLP Solutions and Their Use Cases
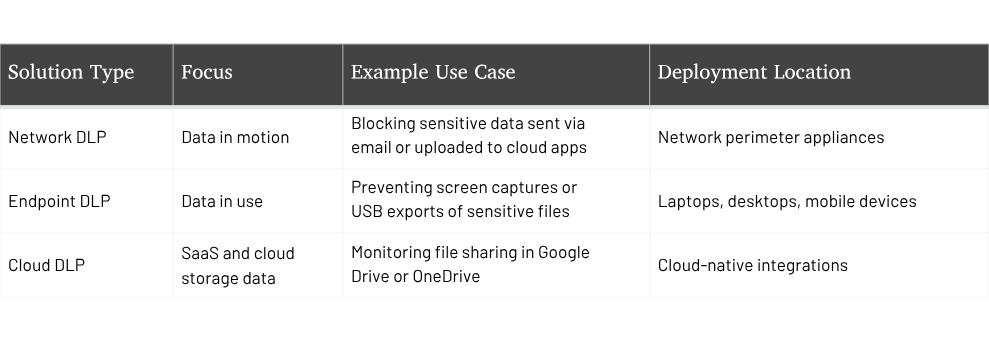
Network DLP
Network DLP monitors data moving across your network, scanning email traffic, file transfers, and uploads to detect sensitive data in motion. It integrates with firewalls and security appliances, blocking unauthorized data transfers and ensuring that sensitive files do not leave the organization without authorization. For example, it can prevent credit card information from being sent outside the company via email.
Endpoint DLP
Endpoint DLP protects data at the device level by monitoring user activities on laptops, smartphones, and tablets. It can detect and prevent actions like copying sensitive files to USB drives, taking screenshots of confidential documents, or printing restricted information, which is particularly valuable in remote work environments where employees use a variety of devices that require monitoring to maintain data security.
Cloud DLP
Cloud DLP focuses on protecting data within cloud applications, like Google Workspace, Microsoft 365, and Slack, where traditional data loss prevention tools often fall short. It monitors file sharing, document collaboration, and cloud storage activities to detect unauthorized access or sharing. For example, Cloud DLP can flag attempts to share confidential HR documents through personal Google Drive accounts, helping maintain compliance while supporting the agility of cloud-based workflows.
How Doppel Complements Data Loss Prevention
Doppel extends traditional data loss prevention by addressing phishing, impersonation, and fraudulent websites that often lead to data breaches. Doppel identifies and removes phishing domains, fake social media accounts, and fraudulent websites that attackers use to steal credentials or exfiltrate data. These threats often bypass traditional DLP tools because they exploit human trust rather than technical vulnerabilities.
By stopping phishing and impersonation attempts before they lead to data leaks, Doppel protects your brand and reduces the risk of credential theft, ensuring your organization’s DLP strategy is comprehensive and effective. See how Doppel helps detect and stop digital impersonation to strengthen your security posture.
Data Loss Prevention Best Practices
- Identify and classify sensitive data to prioritize protection.
- Apply least privilege principles to control data access.
- Train employees to recognize phishing and suspicious activities.
- Monitor and audit data movements continuously.
- Regularly update policies to address new threats and compliance requirements.
- Integrate DLP with broader security strategies, including zero trust and brand protection.
Frequently Asked Questions
What does DLP stand for in cybersecurity?
DLP stands for Data Loss Prevention, a comprehensive strategy that uses policies, monitoring, and tools to stop unauthorized access, sharing, or transmission of sensitive data. It helps organizations proactively protect critical data, maintain customer trust, and comply with regulations.
What kinds of data does DLP protect?
DLP protects sensitive data, including personally identifiable information (PII), like customer names and Social Security numbers, health records (PHI), payment card data, intellectual property, such as proprietary designs or source code, and confidential business documents. Securing this data helps prevent fines, reputational damage, and business disruption.
How does DLP differ from encryption?
Encryption protects data by converting it into unreadable code during storage or transmission, ensuring that even if stolen, the data remains inaccessible without decryption keys. DLP, in contrast, actively monitors and enforces policies to prevent unauthorized sharing or movement of sensitive data before a breach can happen, acting as a frontline defense in data security.
Can DLP prevent insider threats?
Yes, DLP can help prevent insider threats by monitoring unusual or suspicious activities, such as employees downloading large amounts of data, emailing confidential files to personal accounts, or using unapproved storage devices. By detecting these behaviors early, DLP allows security teams to take swift action and prevent leaks caused by intentional or accidental insider actions.
The Future of Data Loss Prevention
As businesses continue to adopt remote work and undergo digital transformation, DLP will evolve with AI-based tools that offer adaptive, real-time protection against emerging threats. DLP will remain a critical part of your brand protection and compliance efforts, supporting secure operations in a digital-first world.
To strengthen your data protection and brand security, gain a broader understanding of our cybersecurity solutions and discover how Doppel can complement and enhance your DLP strategy today.
How many threats is your org facing?
Paid ad scams are designed to exploit digital advertising platforms by generating fake engagement, misleading consumers, or stealing advertising budgets.



.svg)
.svg)