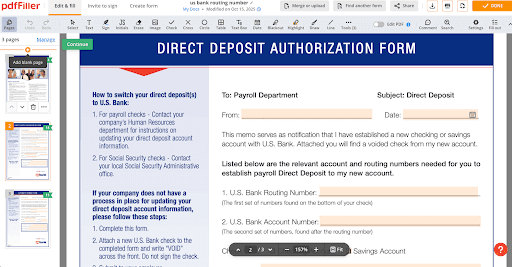
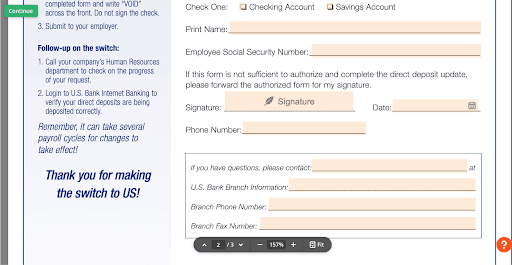
In a routine sweep, Doppel analysts uncovered a fillable direct-deposit template purporting to be from a major U.S. bank sitting on a public document editor — the kind of file anyone can find with a basic Google search.
The form was fully editable, complete with fields for routing and account numbers and even Social Security number collection. In the wrong hands, that single template is enough raw material for account takeovers, counterfeit paperwork, ACH and payroll fraud, and micro-deposit abuse. It’s a stark illustration of what we see daily: official-looking documents on the open web that make social engineering look legitimate and make fraud scale.
Social Engineering is hiding in plain sight
Document scams aren’t limited to obscure corners of the internet. Public-facing PDF editors and document-sharing sites make it simple to download and alter branded forms, invoices, remittance instructions, and KYC templates. Because the files live on the open web — not a secure portal — they’re easy for threat actors to weaponize in targeted outreach to customers, employees, and finance teams. That ease of discovery, combined with the growing availability of AI tools for forgery and content customization, has turned document fraud into a force multiplier for social-engineering campaigns.
The document scam threat is accelerating
Independent data backs up what our analysts are seeing. Entrust’s 2025 Identity Fraud Report found that deepfake attempts occurred every five minutes in 2024, and digital document forgeries rose 244% year over year — a shift that puts well-designed digital paperwork at the center of modern fraud.
Meanwhile, Sumsub’s 2025 trend data reports synthetic identity document fraud surged by more than 300%, driven in part by generative AI that can fabricate convincing IDs at scale.
Put simply: attackers no longer have to convince you their email is real; they show you a form that looks real. And if the paperwork appears to match your brand or your processes, defenses that depend on human judgment alone will fail.
Why document scams work
- Trust by design. Official-looking templates inherit brand trust. Logos, layout, and tone lower skepticism.
- Frictionless edits. Fillable fields and lightweight PDF editors make it trivial to swap in new account details or victim PII.
- Multi-surface delivery. The same forged doc travels through email, messaging apps, social DMs, and even paid search ads, reaching victims where they aren’t expecting risk.
- Process alignment. Paperwork aligns to legitimate workflows (e.g., vendor onboarding, payroll setup, remittance changes), which means fewer “this looks off” alarms.
How Doppel stops it (and why a document is just the first clue)
Doppel continuously monitors publicly accessible document hosts, cloud shares, and web properties to detect branded templates, i.e. invoices, remittance forms, KYC packets, “setup instructions,” and more.
We use text, logo, and layout signals to flag abuse, then link each suspicious document to the broader infrastructure behind it: lookalike domains, paid ads, social accounts, telco numbers, and malicious email senders. Instead of reacting to an isolated PDF, security teams see the whole campaign and can disrupt it at the node where it spreads.
Under the hood, Doppel’s AI-native engine and graph-driven intelligence correlate signals across channels — domains, social media, paid ads, telco, dark web, and more — so analysts don’t have to stitch together a thousand alerts by hand. Our real-time Threat Graph maps attacker infrastructure from lure to monetization and enables bulk, prioritized takedowns that reduce dwell time and repeat abuse.
In practice, that means the editable “bank” form you saw in the lede becomes a pivot: from that artifact, we can surface the typosquatted domain hosting it, the Telegram handle recruiting victims, the ad units driving traffic, and the phone number used to “verify” transfers — and then dismantle the lot.
What you can do now
While Doppel hunts the infrastructure, there are steps every organization and user should take to blunt document-led scams:
- Verify before you open or share.
- Check the sender’s full email address, not just the display name.
- Hover over links before clicking; confirm destinations match official domains.
- Treat attachments with caution. Most genuine onboarding and banking paperwork is delivered via secure portals, not email attachments.
- Ensure the request aligns to a known business process (e.g., payroll change via HR portal, not a text message).
- Harden devices and accounts.
- Keep browsers, office suites, and PDF readers patched.
- Enable reputable anti-phishing/anti-malware protections.
- Turn on two-factor authentication (2FA).
- Even if credentials leak via forged paperwork, strong 2FA blocks logins. Prefer an authenticator app over SMS.
- Establish “change control” for money movement.
- Any vendor or payroll remittance change requires out-of-band confirmation to a verified contact at a verified number.
- Instrument visibility where attacks happen.
- Expand monitoring to paid search, social DMs, messaging apps, and fringe platforms — the places document lures often originate.
The takeaway
A convincing document is no longer a one-off artifact; it’s the starter pistol for a multi-channel fraud campaign. The editable direct-deposit form we found is a reminder that the “paperwork” your teams and customers trust may already be circulating in the open, and that attackers are using it to front-run your controls. The good news: When you can see the campaign, including the files, the domains, the accounts, the ads, and the numbers, you can stop it faster.
See how Doppel links suspicious documents to the domains, ads, accounts, and numbers behind them — and removes them at scale. Request a demo.