Major platform incidents are catnip for phishers. Expect “AWS security notice,” “restore access,” and “refund due” attack campaigns across email, SMS, and messaging apps in the days ahead. Use rapid, threat‑informed simulations to harden your first line of defense, your people, before the scams scale
What happened, and why it matters for social engineering
On October 20, AWS experienced a widespread U.S.-East-1 outage that rippled across popular apps and services. Coverage noted millions of user reports and warned affected organizations to expect degraded performance during restoration — prime conditions for scammers to rush in with “we can fix it” phish. In other words: confusion + urgency + brand trust = the perfect phishing storm.
Note: This was an outage, not a data breach. But phishers will happily mislabel it a “breach” to juice clicks.
Why attackers love headlines like this
When something as big as AWS blips, adversaries reach for the same playbook:
- Authority pretext: “AWS Support” or “Your SaaS Security” urges you to verify identity or reset access due to the incident.
- Time pressure: “Action required in 30 minutes to prevent account lock.” motivates users to act before they think.
- Multi-channel delivery: The lure isn’t just email anymore, expect voice calls, SMS, WhatsApp, Telegram, and even fraudulent, imitation status pages.
- Infrastructure camouflage: Look‑alike domains (aws‑status[.]help), typosquatting, spoofed numbers, and cloned support flows that feel almost right.
And attackers run campaigns, not one-offs. They mix domains, social accounts, paid ads, phone numbers, and encrypted chat handles into a single operation, all with the intent of confusing targets into believing it’s the real thing.
The likely lures you’ll see this week
These are just a few examples of the attacks that will surface in the coming days. Use this as a quick threat brief for your SOC, help desk, and comms teams. Then, test how your employees would fare against these types of attacks by running phishing simulation campaigns:
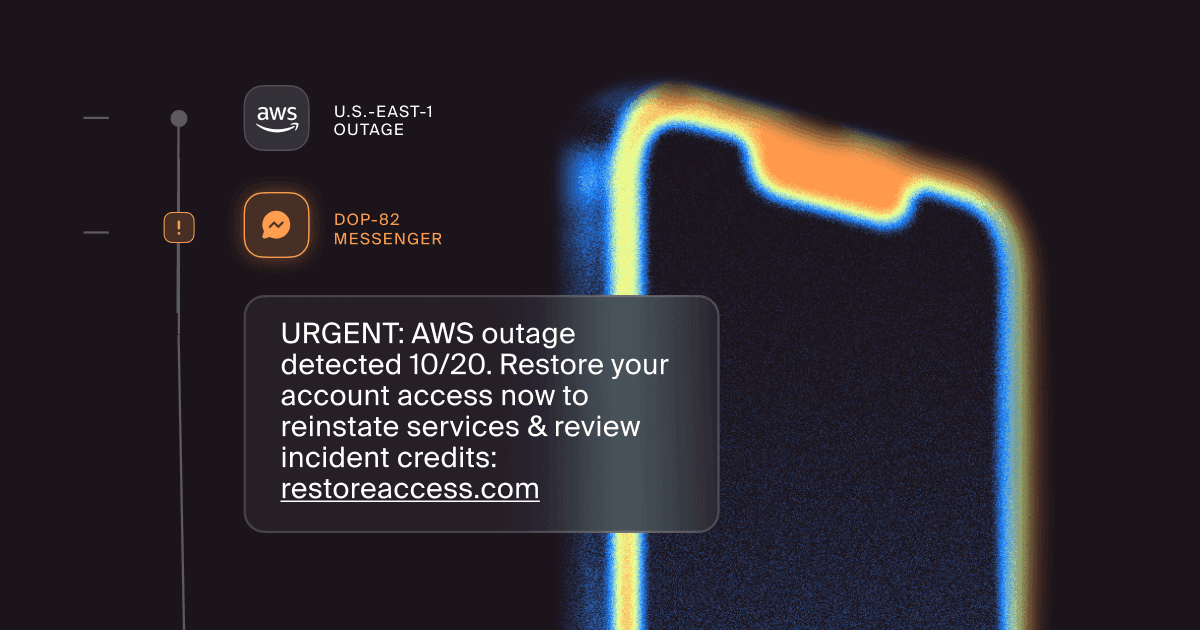
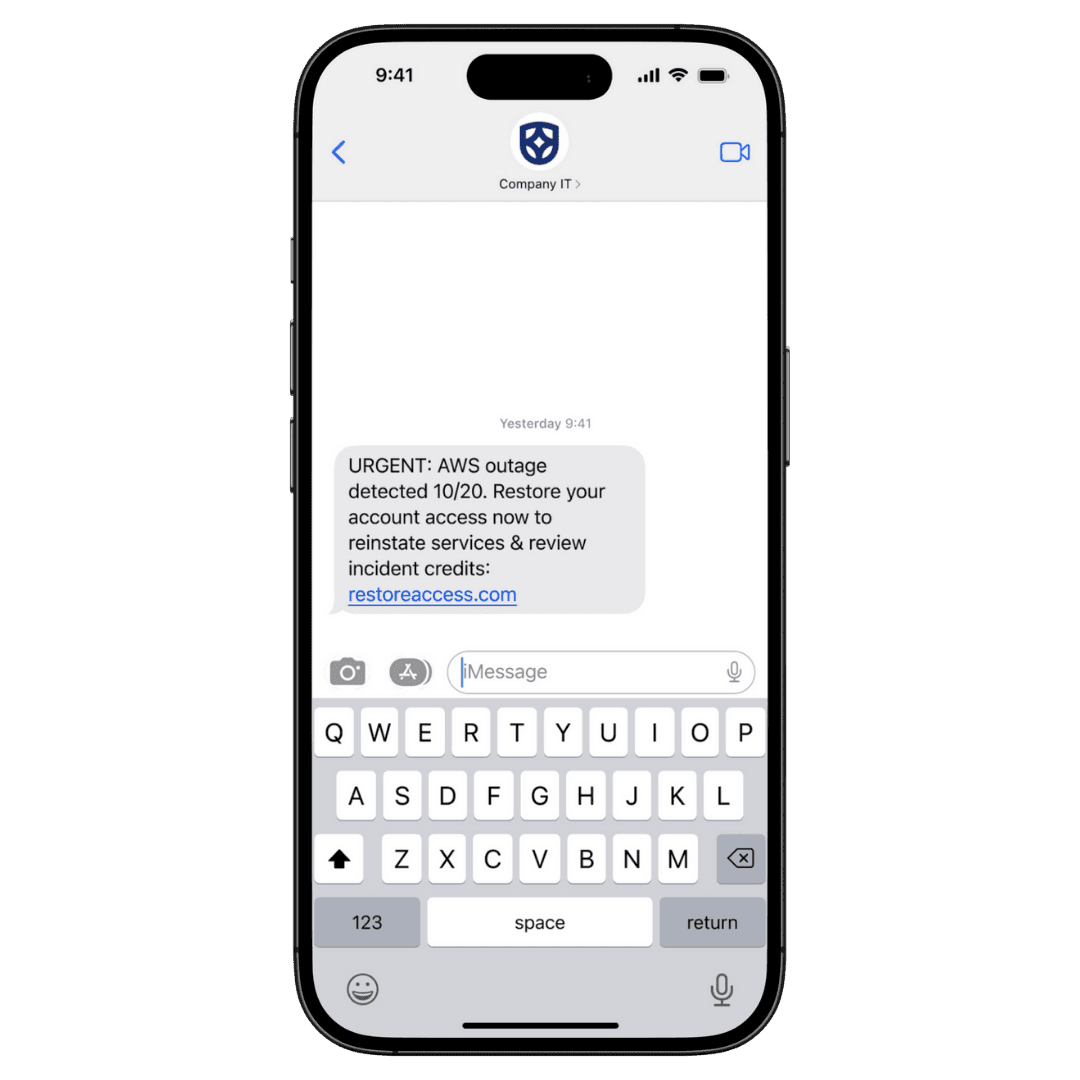
- “Restore access” links for Slack, Okta, Microsoft 365, or internal tools “impacted by AWS.”
- “Security refund / incident credit” forms asking for payment details.
- “Urgent token reset” prompts for API keys, OAuth tokens, or MFA seeds.
- Fake AWS/CloudFront status updates redirecting to credential harvesters.
- Spoofed help desk calls (vishing) offering to “walk you through” an account unlock.
Here's just one example:
What security teams should do in the next 72 hours
Preempt the pretexts
- Publish a short, plain‑English internal bulletin alerting people to be extra cautious: We will never ask for passwords, 2FA codes, or payment info via email/SMS because of the AWS incident.
- Share a list of known or obvious lookalike domains, along with the only legitimate domains to reference.
- Add temporary email banners through your email security provider for messages mentioning “AWS outage,” “restore,” “incident credit,” or “unlock” to encourage extra vigilance.
Correlate beyond email
Pull indicators from domains, social, ads, SMS/voice, and fringe chat apps; treat them as a single campaign, not separate alerts. This is where graph-driven intel shines: it links lures, infrastructure, and personas so you can disrupt nodes, not chase artifacts.
Train fast with threat-informed simulations
Convert the above lures into simulations that mirror what’s circulating right now. This moves you from awareness to measurable resilience, and teaches your employees to be vigilant in a safe environment.
Turn today’s headlines into tomorrow’s readiness: prepare by running a phishing simulation campaign
Here’s a 30-minute plan your team can execute today:
Step 1: Pick 2–3 realistic pretexts
- Email + SMS: “AWS outage, verify to restore Slack access”
- Email + WhatsApp: “AWS service credit, validate account for refund”
- Vishing follow-up: “CloudOps calling about your token reset”
Step 2: Launch multi-channel tests
- Target high-risk roles (IT admins, Finance/AP, Support) first.
- Measure: reporting rate, time-to-report, and time-to-response (help desk + SOC).
- Sample prompts you can paste into Doppel Simulation:
- Create an SMS phishing simulation themed around the Oct. 20 AWS outage. Goal is for IT admins and Finance/AP to complete a “restore access” flow that requests SSO credentials, then pushes a fake incident credit form.
- Build an email simulation that impersonates an internal help desk from [Company Name]. Pretext: urgent OAuth token reset due to “AWS breach”. Include a shortlink to a cloned Okta portal and a 2-minute escalation warning.
- Preview your simulation campaign. It might be a voice call that sounds something like this:
Step 3: Coach and close the loop
- Give role-specific feedback and educational content based on results.
Doppel Simulation makes this fast: generate lures from natural‑language prompts, mirror what’s in the news, and test across email, SMS, messaging apps, and voice. You can even clone real threats seen by Brand Protection to test your users safely against the exact tactics adversaries use. Preview it today.