Information Leakage
Overview of Information Leakage
Information leakage is a slippery slope. A small information leak could lead to potential data loss and increased digital risk. According to the Verizon 2025 Data Breach Investigations Report, 22% of data breaches resulted from credential abuse. Although this is down from their 2023 report (49%), it’s still important to keep your credentials secure to prevent information leakage.
In the table below, you’ll find a quick summary of the three different types of information leakage, including accidental, malicious, and insider threats, followed by a more in-depth overview of how they can impact an organization.
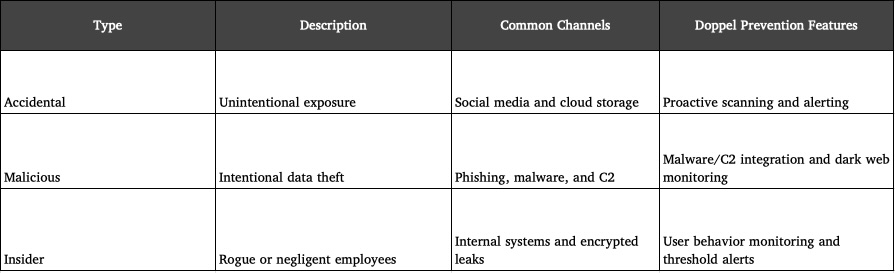
Accidental Exposure
Accidental leaks, also known as unintentional exposures, happen all the time due to human error. For instance, an employee takes a selfie at their desk and has a customer’s Salesforce profile pulled up in the background. If anyone zoomed in on the screen, it would reveal the customer’s personally identifiable information (PII), resulting in a potential leak.
Another way information could be unintentionally shared is through screenshots of reports. If internal data was contained in the reports, and then shared with the wrong Jim’s email, this is an accidental data leak.
The last accidental exposure example we’ll share involves cloud storage misconfigurations. Most organizations have some type of cloud storage like AWS S3 to share internal assets with coworkers. However, if the file was set to public, then the internal customer data is publicly accessible through the cloud to anyone.
Each one of these could easily escalate and result in a data breach if not correctly monitored and resolved. Luckily, Doppel proactively scans social posts, public cloud folders, and collaboration tools to detect exposed data before it spreads.
Malicious Breaches & Exfiltration
Outside of accidental leakage, there are malicious breaches and external threat actor infiltration where attackers are actively trying to break into systems and networks. One malicious breach example includes phishing credential harvesting, where attackers trick employees into sharing credentials.
Malicious actors could also use malware keylogging to capture keystrokes and identify credentials to exfiltrate data for financial gain. There are several other means of maliciously gaining sensitive data, but the last example we’ll share is where threat attackers use command-and-control (C2) channels like the one used for HAMMERTOSS malware, where they used social channels to exfiltrate stolen data through backdoor commands.
To combat malicious information leakage, Doppel integrates with malware and C2 detection tools to intercept these exfiltration attempts in real time.
Insider Threats
Lastly, information leakage can result from rogue or negligent employees who intentionally, or unintentionally share sensitive data for malicious payback or financial purposes. For example, a previous employee was let go but has retained access to customer information, and in their anger forwards the lists to your competitor.
Another incident could be an employee who accidentally chose the wrong email address and didn’t notice before sending an internal-only document to an external vendor.
For our final common insider threat example, an employee uses encryption to hide stolen data while sending it externally to avoid detection and critical information is leaked.
All these incidents may have been avoidable with the proper detection. Doppel provides proactive defense by monitoring user behavior, flagging suspicious activity, and detecting potential leaks across systems and dark web channels.
Causes & Risk Factors
Information leakage can happen due to many different factors, but one of the biggest is human error or negligence. According to CyberRisk Alliance and SC Media, 95% of breaches involved human mistakes in 2024. These errors included misconfigurations in cloud systems and security tools and inadequate access controls. With high pressure from remote work, bring your own device (BYOD), and shadow IT, cybersecurity teams are managing a lot and too often with limited resources, leading to mistakes.
To help catch and mitigate these errors, Doppel provides services to review and counsel on risk assessments, least-privilege access, and user-behavior monitoring.
Request a demo today to learn more about Doppel’s proactive defense.
Social Media & Paste Sites
Open platforms such as social media and paste sites amplify leaks. Social media sites like LinkedIn, Twitter, and Facebook are more vulnerable due to their highly visible nature which can be indexed by search engines and scraped by attackers, making even small leaks widely accessible. Each post is also able to be easily shared through retweets or reposts, expanding the poster's original reach.
Paste sites, like Pastebin, JustPaste.it, and GitHub Gist, may make your organization more vulnerable to information leaks as developers often leverage paste sites to share logs or error dumps and unintentionally expose IP addresses, API keys, or customer data.
Additionally, malicious actors use machine learning tools and paste sites to post stolen data samples to prove breaches or sell data. They can also utilize data from social media or paste sites for social engineering, phishing, or targeted attacks against employees and high-level executives.
Real-time monitoring of social platforms and paste sites helps organizations detect leaks early and prevent exploitation. Doppel’s brand protection platform actively scans social media and paste sites for your brand mentions, PII, and credentials, providing you with real-time alerts to mitigate risks before exploitation.
Code Repositories & Public Cloud
Another way information is often leaked is through inadvertent commits of API keys and product secrets to GitHub when developers are working on code. Protecting source code is crucial to preventing unauthorized access and misuse. Still, even with the proper safeguards, proprietary code can leak through misconfigured S3 buckets or other means.
Doppel integrates with GitHub, S3, and other platforms to quickly detect exposed secrets and credentials and alerts you as soon as possible to minimize risks.
Dark Web & Forums
Once information is leaked, those stolen credentials are often housed on underground forums and marketplaces on the dark web to be sold. With credential leaks resulting in a large percentage of data breaches, it’s important to regularly monitor these channels to discover any information leaks.
If you are interested in gaining better dark web visibility with credential monitoring, Doppel provides brand and executive protection for round-the-clock protection to prevent financial loss, reputational damage, and operational disruption.
How to Prevent Information Leakage
When it comes to preventing information leakage, we recommend taking a layered defense approach by implementing strong security policies, monitoring and takedown tools, and employee training. Creating proper security protocols for guardrails is important, but we know that human error can lead to information leakage. That’s where employee training and continuous monitoring are required to fortify your defenses
With Doppel, you’ll get live scanning across your online channels from social media to NFTs to the dark web with automated take downs, triaged alerts, and risk prioritization workflows to ensure your digital presence and your brand stay secure.
Best Practices
Some best practices to consider for information leakage prevention include:
- Creating and enforcing clear security policies that are easy to understand
- Enabling least-privilege access management to reduce unnecessary data exposure
- Running regular employee training for data handling and social media hygiene
- Automating monitoring and alerts for the brand and executive digital presence
- Having a rapid response and takedown process for when incidents occur to minimize leaks
For more best practices on how you can protect your brand, check out Doppel’s blog.
Information Leakage & Doppel
Information leakage can stem from accidents, malicious actions, or insider threats and can result in credential leaks, reputational damage, and regulatory risk. Organizations must view information leakage as an ongoing digital risk requiring consistent monitoring and rapid action.
Doppel’s 24/7 visibility, automated mitigation, and risk reduction across surface, deep, and dark web channels will block leaks and prevent breaches. Our platform provides proactive defenses for your digital presence to detect threats across domains, social media, and email, identifying fraudulent accounts, typosquatted domains, fake numbers, and deepfake content for comprehensive protection. We also combine AI and our expert insight to detect phishing, deepfakes, and synthetic profiles.
Ready to stop information leakage before it happens? See Doppel in action.
Want to continue to learn more terms and stay on the cutting edge of cybersecurity? Check out the Doppel-pedia.
How many threats is your org facing?
Paid ad scams are designed to exploit digital advertising platforms by generating fake engagement, misleading consumers, or stealing advertising budgets.
FAQ
What is information leakage?
Information leakage is when sensitive data is exposed unintentionally or intentionally, including credential leaks, confidential document exposures, and insider leaks. For example, an employee downloads and prints a sensitive, internal report and brings it out of the office without the proper approvals. This is one way information can be leaked.
How is information leakage different from a data breach?
Information leakage can be accidental, such as oversharing on social media, or intentional, like malware theft. On the other hand, a data breach is almost always unauthorized access with malicious intent. The two are connected, but normally an information leak comes before a data breach.
What are the signs of information leakage?
Signs of information leakage include:
- Suspicious social media posts
- Unexpected mentions of your brand
- Abnormal insider behavior
- Unusual or excessive data exfiltration
- Publicly posted credentials or secrets
- Sightings of your customer or employee information on the dark web.
How can Doppel help prevent information leakage?
Doppel provides automated monitoring, dark web visibility, rapid takedown, and risk mitigation workflows to prevent and manage information leakage effectively.
Our platform provides proactive defenses for your digital presence to detect threats across domains, social media, email, and the dark web, identifying fraudulent accounts, typosquatted domains, fake numbers, and deepfake content for comprehensive protection. We combine AI and expert insight to detect phishing, deepfakes, and synthetic profiles.
Plus our human-trained LLM models analyze images, video, text, and metadata while adapting to evolving threats. And we disrupt attacks at the source by mapping and dismantling cybercriminal infrastructure, automatically taking down malicious domains, emails, and fake profiles.



.svg)



.svg)